 A few months ago, I got an annoying piece of code on my laptop known as the FBI Moneypak virus. It locked down my laptop screen and demanded a ransom for me to have it unlocked – right in the middle of midterm week. Thankfully the virus was easy to remove and I was able to boot my laptop in safe mode before running anti-virus software to remove it. Different variants of the Moneypak virus began popping up over the internet, each strain slightly different and more difficult to remove until two months ago when an infinitely more dangerous began to appear. The Moneypak virus scares victims into thinking their computer will be permanently locked, covering their screen with a digital ransom note that cannot be removed until a victim pays up. Even if you don’t pay the money, or if you remove the virus, your files are (usually) safe. CryptoLocker however is the complete opposite.
A few months ago, I got an annoying piece of code on my laptop known as the FBI Moneypak virus. It locked down my laptop screen and demanded a ransom for me to have it unlocked – right in the middle of midterm week. Thankfully the virus was easy to remove and I was able to boot my laptop in safe mode before running anti-virus software to remove it. Different variants of the Moneypak virus began popping up over the internet, each strain slightly different and more difficult to remove until two months ago when an infinitely more dangerous began to appear. The Moneypak virus scares victims into thinking their computer will be permanently locked, covering their screen with a digital ransom note that cannot be removed until a victim pays up. Even if you don’t pay the money, or if you remove the virus, your files are (usually) safe. CryptoLocker however is the complete opposite.
Most people are infected through spam mail. Clicking on attachments from people you don’t know, or from friends or family you weren’t expecting to get attachments from is a very easy way to get infected. You can also catch the virus from less harmful malware already installed on your computer. You can also get the virus from computers that share resources on your network. The virus spreads similarly to the Autoplay malware that made its way around campus last semester, it you share network drives, USBs drives or email and receive attachments often, you are also liable to get infected.
This virus is a nasty one, there’s no other way to put it. Very rarely do victims of this virus know when they’ve been infected. Once it gets onto a computer, it targets files with the following extensions:
*.odt, *.ods, *.odp, *.odm, *.odc, *.odb, *.doc, *.docx, *.docm, *.wps, *.xls, *.xlsx, *.xlsm, *.xlsb, *.xlk, *.ppt, *.pptx, *.pptm, *.mdb, *.accdb, *.pst, *.dwg, *.dxf, *.dxg, *.wpd, *.rtf, *.wb2, *.mdf, *.dbf, *.psd, *.pdd, *.pdf, *.eps, *.ai, *.indd, *.cdr, *.jpg, *.jpe, *.jpg, *.dng, *.3fr, *.arw, *.srf, *.sr2, *.bay, *.crw, *.cr2, *.dcr, *.kdc, *.erf, *.mef, *.mrw, *.nef, *.nrw, *.orf, *.raf, *.raw, *.rwl, *.rw2, *.r3d, *.ptx, *.pef, *.srw, *.x3f, *.der, *.cer, *.crt, *.pem, *.pfx, *.p12, *.p7b, *.p7c.
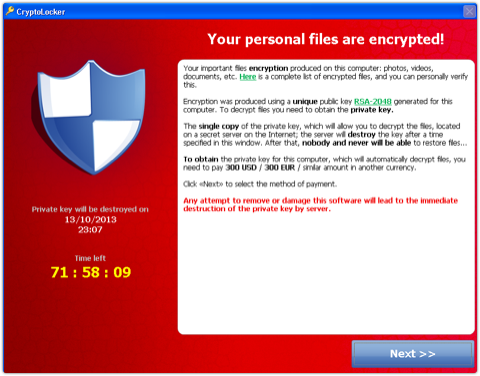
The virus then proceeds to encrypt them with RSA (Rivest Shamir Adleman) and AES (Advanced Encryption Standard) encryptions. Any and everything attached to your computer will be infected. Cloud storage won’t necessarily save your files – people who installed have Dropbox on their computers will have the files in their account encrypted. Attached USB or disk storage will also be encrypted. Any new files you create with the above file extensions will also be encrypted, effectively rendering your computer files useless.
Once CryptoLocker has successfully infected all the files on a target PC, it displays a warning message, giving victims 72 hours to pay around $300 or their files permanently encrypted. They aren’t bluffing. There are numerous reports of people and businesses loosing important files because they didn’t pay the ransom. It’s much worse for people who attempt to (or even accidentally) remove the virus from their computers.The ransom can increase anywhere between 3 and 10 times the initial value of $300. Only an infected computer can access the website to pay the ransom to unencrypt their files, but for the people who’ve accidentally uninstalled the virus, don’t worry.The creators of the virus realized that they were missing out on income and so, provide victims with a link to reinfect their computers so that they can pay up.
There’s a serious debate over whether or not people should pay money to retrieve their files. The argument against paying is that giving up the money encourages the hackers to target more people and continue to update the virus to earn more money. Who wouldn’t – the creators of CryptoLocker are said to have earned upwards of $5 Million in on year. For people who risk losing irreplaceable family photos, financial documents and client files worth thousands of dollars each though, there’s no other option than to pay the money.
Open attachments at your own risk.
Sources:
- http://krebsonsecurity.com/2013/11/cryptolocker-crew-ratchets-up-the-ransom/
- http://arstechnica.com/security/2013/10/youre-infected-if-you-want-to-see-your-data-again-pay-us-300-in-bitcoins/
- http://krebsonsecurity.com/2013/11/how-to-avoid-cryptolocker-ransomware/
- http://blog.malwarebytes.org/intelligence/2013/10/cryptolocker-ransomware-what-you-need-to-know/
- http://www.bleepingcomputer.com/virus-removal/cryptolocker-ransomware-information
- http://www.makeuseof.com/tag/cryptolocker-is-the-nastiest-malware-ever-heres-what-you-can-do/



