The English department is developing a new Creative Writing course. Please take a minute to fill out this survey to help with its development. Thank you!
Announcement, Job and Experience Opportunities
There are some upcoming job seeking opportunities that I wanted to let you all know about. The Civil Service 101 presentation opens the doors about how to seek Civil Service jobs, and the CUNY Service Corp is a great opportunity to learn skills while gaining invaluable experience for your resume.
Civil Service 101 for LGBTQ+ Students and Allies (Click here to register)
Tuesday, December 7th 1:00-2:15 pm
Are you interested in having a fulfilling career? Are curious about what City jobs are like for members of the LGBTQ+ community?
The New York City government offers more than 2000+ job titles in 80+ agencies. Come see where your professional journey can take you at Civil Service 101 for LGBTQ+ Students and Allies, a virtual event on December 7th from 1:00-2:15 pm.
The Department of Citywide Administrative Services will discuss Civil Service career options in NYC and how to apply for them. There will also be a representative from the Department of Health & Mental Hygiene who will discuss the LGBTQ+ Employee Resource Group, jobs currently available, and services that the department provides for the LGBTQ+ community.
Not a member of the LGBTQ+ community? No worries, all are welcome!
Sponsored by the Academic Minor in Gender & Sexuality Studies
CUNY Service Corp
Benefits? Transferable Skills, resume building, career path and connections,and get involved with their community.
We have an alumni cohort of 1,000+ past members. Since August of 2013, CUNY Service Corps members have completed over 1,000,000 hours of service to NYC at over 150 nonprofits, government agencies, and hospitals. In the past, we have worked with Girls Who Code, Federal Reserve, Brooklyn Navy Yard, and research projects at City Tech ( i.g. SOLAR Decathlon).
Application is open to all City Tech students for Spring 2022 (Dependent on program eligibility):www.citytech.cuny.edu/servicecorps
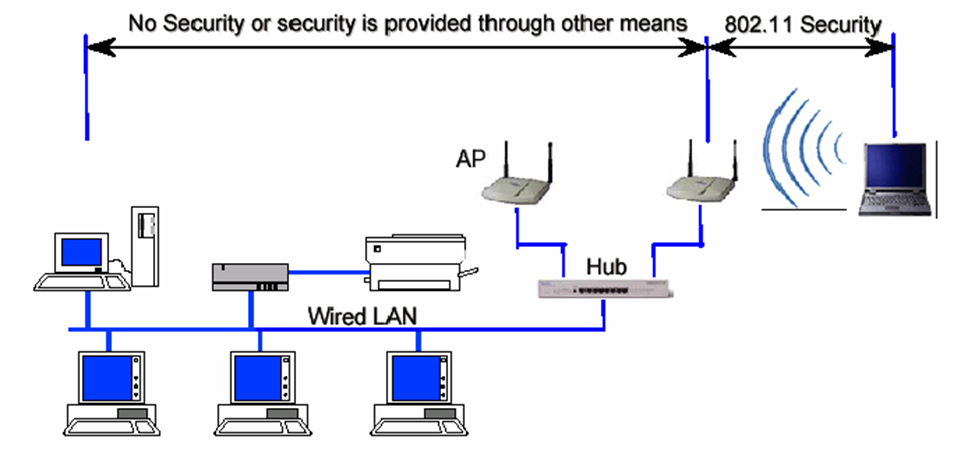
1500 word manual instruction on secure computer network/wireless
TO: Prof. Jason Ellis
FROM: Kanak Das
DATE: 12/01/2021
SUBJECT: 1500 word instruction manual on Secure Computer network/Wireless
Encryption is one of the major subject to talk about in wireless security, Because, all wireless computers are radio transmitters and receivers, anyone can listen to the information that are being transfer or received, that’s why it’s important to have encryption enable on wireless network. So, that way even if the other people hear about the information, they would not be able to see the information. Only people will have access are the ones with proper passwords or proper wireless configuration.
Another major topic in wireless network is Hacking. For example, if you connect to public network, it can be easily intercepted by cybercriminal, where your personal data could be at risk. Whenever there is free public wi-fi, once you connect to these fake network everything you do online is monitor by cybercriminal. Who can scan your activity such as social media log in information. Cybercriminal can even easily transfer viruses, or other unnecessary software to your computer. That can cause serious damage to your computer and can get through your personal information.
Despite the fact these public networks can be harmful, there are ways to stay safe on public wi-fi. such as:
- Verify your connections, be sure to ask an employee what the actual public Wi-Fi is, in order to avoid fake network.
- Avoid checking sensitive or personal data, unless it’s necessary, avoid logging in Facebook, email and more importantly financial accounts while on public Wi-fi.
- Turn off Sharing, In your computer or the social media you are using there’s Sharing ON and OFF option. Turned that off while you are on public network.
- Turn your Wi-Fi off when you are done with your work. That can prevent falling your personal files and information on wrong hand.
So, now that there are some disadvantages of wireless security, it needs of improvement of protecting wireless data while they are in transit between a client and wireless access point.
- Techniques and Technology can be applied are:
- Use dynamic encryption key.
- Include real authentication key.
- Use strong encryption.
- Use improved cryptographic integrity protection for data frames.
- Improve session initiation.
- Use Strong Passwords.
- Have your Email connected to trusted device.
Another security technique can be applied is WPA which is Wi-fi Protected Access. WPA improve security by adding authentication Protocol for access control. It ensures the secure wireless communication. WPA support for temporal key integrity protocol TK IP which can be implemented in software with just firmware update. Along with that it also provides integrity checking using MIC, which is Message Integrity Code.
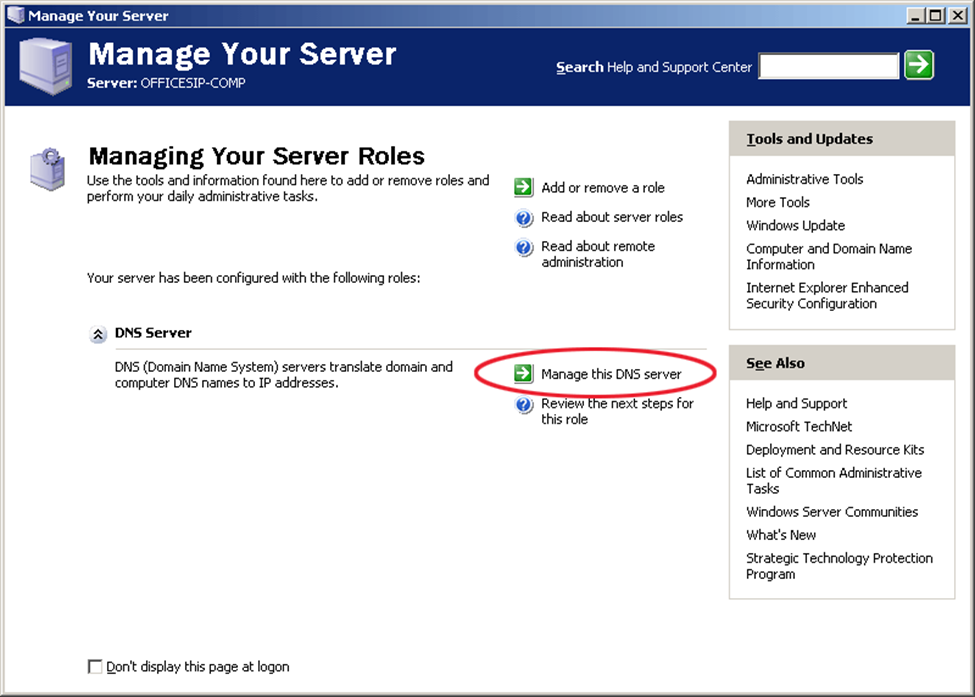
Configuring DNS on Windows, because The Domain Name System (DNS) is the protocol that makes the Internet usable by allowing the use of domain names. Its one of the safe zone to configure files or extract file.
Open the Server Manager from the task bar.
Click on DNS/ Right Click your server / select DNS Manger/ Click the Action Tab/ Select Configure a DNS Server.
-Select Configure a DNS Server in Windows Server 2012
The Configure DNS Server Wizard will come up click Next to continue and select one of the following actions:
– Create a forward lookup zone
A forward lookup zone is a DNS function that takes a domain name and resolves it to an IP address.
– Create forward and reverse lookup zones
A reverse lookup zone is a DNS function that takes an IP address and resolves it to a domain name.
– Configure root hints only
Root hints only Will have the IP addresses of DNS servers where records can be acquired.
This is the Configure DNS Server Wizard screen output in Windows Server 2012
Select where the DNS data will be maintained for your network resources, and then Click Next
Selecting a Primary Server location in Windows Server 2012
Enter your new zone name, in this case, your domain and Click Next.
This is the zone name insert field when configuring DNS in Windows Server 2012
Create a new zone file or use an existing one from a different DNS server
Creating a Zone file when configuring DNS in Windows Server 2012
Next you select how your server will respond to Dynamic Updates.
Select the do not allow Dynamic Updates option while Configuring DNS in Windows Server 2012
Select whether your DNS server should forward queries or not. If you choose YES, type the IP of the server and click Next. If NO, select No, it should not forward queries and Click Next.
Select one of the options to configure forwarders when Configuring DNS in Windows Server 2012
Click Finish and you’re all set.
Completing the DNS configuration in Window Server 2012
Furthermore, one of the case study I did, to learn this implementation even better is that there is Wi-Fi provider known as Web Titan. Web titan cloud for Wi-Fi is a web content filtering and network security solution for Wi-Fi providers. This is based in London UK. Selfridges ensure that guests and staff don’t have encounter malicious sites or view inappropriate content while using their Wi-Fi network.
According to this case study this is good Wi-Fi provider for business. Some of the reasons are, it provides a safer, faster and more secure environment for your hotspot guests and finally it allows you to control the content that you allow your guests to access. You can control multiple locations and routers And Web Titan Cloud handles any volume of usage. The product has extensive reporting, easily showing you usage and traffic. It also supports dynamic IPs and works with any device that joins your network. Another feature is that all of this protection and filtering comes without any compromise to speed.
Moreover, Security in public places has become one of the major issue in Wireless security field. There have been many references on how the problem can be fixed. Top of all that VPN also known as Virtual Private Network, can be one of the strongest ways to secure our Network. This is also can be called as Layer 3 security which left the IP network vulnerable to attacks. For instance, if you need to check sensitive data such your banking or any financial account while on public Wi-Fi use Virtual Private Network. Even if a cybercriminal positions himself in a middle of your connections, your data or files will be strongly encrypted.
In conclusion, securing wireless networks can be useful and difficult and harmful at the same time, but it all depends on how carefully we are using it. As I discussed on my previous paragraph there many techniques and method we apply in order to protect our privacy. There are procedure we can follow to help ourselves in wireless network, to ensure that a wireless network is as secure as possible, network administrator should follow several guidelines.
First, and most importantly the wireless network must be encrypted as I mentioned earlier. For this purpose, it is critical to use WPA based encryption rather than WEP based encryption. Since WEP encryption is severely flawed and can be cracked with free software in jut few minutes.
Second, it is important to remember that the benefits of wireless networking come up with price. To extend this idea more, data that are traveling over wired network, wireless data are much more exposed and open. Even, if wireless data are encrypted, the absence of physical wire network, it bring the hacker one step closer to gaining access to sensitive data.
Finally, a long password should be used for network authentication. The use of very strong password may be inconvenient or bothering for users, but it will help to prevent the hacker from foiling any password cracking attack. As you can see, the use of wireless network can be very beneficial and unfavorable at the same time but it is our choice how we are going to use it for, when to use it and have pick the right moment to value our wireless technology. Technology has changed a lot throughout the years, we don’t know what the technology hold for us in future. But the way our technology growing rapidly it won’t very long until we see something amazing on technology world. Network wireless has improved a lot through the years and surely it will be even better and safer with strong encryption and protected devices, where people can access network and Wi-Fi without any worry or hesitations.
750-1000 Word Expanded definition on Networking Firewall
TO: Prof. Ellis
FROM: Kanak Das
DATE: 12/01/2021
SUBJECT: Expanded Definition Term: Networking Firewall
Firewall is one of the important topic on Information technology. The purpose of the memo indicates that the computer or the network we use; how it can protect our information, data and applications. There are also other terms that goes along with Firewall, such as Wireless security, Network Security, Virtual private network (VPN), Virus, Ransomware. Some resources I have used for research to focus on my term is Forcepoint, Vmware, Dictionary.com. the term I have selected to focus is Firewall; A firewall is a network security device that monitors incoming and outgoing network traffic. My interest in computer is mostly network security where firewall comes up big when computer or network requires protection from hackers or malicious users.
“A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules.” “Advanced firewall can no longer single-handedly defend a network against today’s complex cyber threat landscape, these devices are still considered to be the foundational building block for creating a proper cybersecurity system”. From these two quoted definitions we can understand that firewall might protect network from malicious traffic, but it’s still not capable enough to stop higher complicated attack or threat. While in network firewall can be divided int two types of protection proxy and stateful, which decided what to use when, proxy can be regularly use for any kind of websites that the users might think it’s not safe website to work on. On the other hand, stateful monitors the full state of active network connections. This means that stateful firewalls are constantly analyzing the complete context of traffic and data packets.
Moreover “traditional” firewall, a stateful inspection firewall allows or blocks traffic based on state, port, and protocol. It monitors all activity from the opening of a connection until it is closed. Filtering decisions are made based on both administrator-defined rules as well as context, which refers to using information from in previous connections and packets belonging to the same connection.” And “and applications crossing through the network perimeters – especially due to the growing volume of IoT and end user devices – and less overall centralized control from IT and security teams, companies are becoming much more vulnerable to cyberattacks.” These two sentences basically talk about the fact that stateful inspection firewalls and application crossing through a specific network can be harmful for the company and for the applications itself. When data or packets being transfer form one network to another if the stateful firewall don’t investigate those packets or file a company’s or any firms information can be in wrong hands.
For example, in simple terms NAT is used to convert your IP address into your routers IP address , this is done because ipv4 which is a 32 bit IP address is limited and exhausted . Ur private IP address is not recognized by google so yuir router does the talking to the internet. It is like a cell phone which allows u to talk to “google.So” your private IP address is converted into the internet IP address with the help of net masking which u can see on seeing ifconfig which shows that your private IP address is converted into the routers IP address. Basically, when u buy internet connection you are buying an IP address that can talk to the world. ISP has globally bought a range of Ip address from IANA and it is giving u an ipaddress. So all the devices which access internet from ur home would actually be converted into the routers ip address in ur router and those packets are shoots up into the net. So router does the working of a postman when it receives reply from google and internally unmask the Ip address to determine who was the person who send that request.
In conclusion, Firewall term can be referred as where protection is needed. Whether it’s in computer, hardware, software. A firewall acts as a defensive border by helping to protect your computer from hackers, blocking malware from penetrating your system, and removing sensitive data from a compromised system. Such as stateful Firewalls scan each “packet” of data, small chunks of a larger whole, reduced in size for easy transmission, to make sure these packets don’t contain anything malicious. and interacts with the internet they come between you and the internet and thereby prevents direct connections this protects your device’s identity and keeps the network safe from potential attacks.
- “Firewall.” Fine Dictionary, http://www.finedictionary.com/firewall.html.
- “Firewall Definition and Meaning: Collins English Dictionary.” Firewall Definition and Meaning | Collins English Dictionary, HarperCollins Publishers Ltd, https://www.collinsdictionary.com/dictionary/english/firewall.
- “What Is a Network Firewall?” Fortinet, https://www.fortinet.com/resources/cyberglossary/firewall.
- “What Is a Network Firewall?” Fortinet, https://www.fortinet.com/resources/cyberglossary/firewall.
500-Word Summary on Network wirless security
TO: Prof. Ellis
FROM: Kanak Das
DATE: Dec, 1, 2021
SUBJECT: 500-Word Summary of Article About Network Wireless Security
When we talk about network in computer, it also include huge responsibility in security as well as wireless security. It is one of the most important and fundamental topic in Networking. The reason this is an essential research in this topic is because Network security helps in protecting personal data, files, and others important information that is connected to devices. Increasing network security, you decrease the chance of privacy spoofing, identity or information theft and so on. Wireless network has become one of the fastest technologies for everyone’s benefit, which is a Computer Network that allows computing devices to communicate with each other without being connected through physical communications medium, such as networking cable or any involvement of wire. It is usually reply upon radio communication and wireless Network are implemented at the physical layer which is Layer 1 of the OSI model. The importance of wireless security is that it is all in one person under control. The owner can control it from anywhere nearby, without any need of wire or cable. Some of the reasons are, trusted video security solutions, commitment to quality with superior service, for personal protection.
Wireless technologies use radio frequency transmission as the means for transmitting data, whereas wired technologies use cables. Wireless technologies range from complex system, such as WLAN which is Wireless Local Area Network, when we use cell phones and have wireless headphones, through the use of Bluetooth to listen to songs, and other small devices that does not require wire. moreover, we also have, WPA which is wireless Access Point, is hardware device that allows properly equipped computing device to connect wirelessly to a network. Which can be used through router including a radio transceiver to enable wireless communication with client, and where we all use it every single day, commonly known as Wi-Fi. The transport mechanism between devices connect can also have impact on the all devices that connected to each other and any information can be shared easily through this process. Encryption is one of the major subject to talk about in wireless security, Because, all wireless computers are radio transmitters and receivers , anyone can listen to the information that are being transfer or received, that’s why it’s important to have encryption enable on wireless network. So, that way even if the other people hears about the information, they would not be able to see the information. Only people will have access are the ones with proper passwords or proper wireless configuration.
Another major topic in wireless network is Hacking. For example, if you connect to public network, it can be easily intercepted by cybercriminal, where your personal data could be at risk. Whenever there is free public wi-fi, once you connect to these fake network everything you do online is monitor by cybercriminal. Who can scan your activity such as social media log in information. Cybercriminal can even easily transfer viruses, or other unnecessary software to your computer. That can cause serious damage to your computer and can get through your personal information.
Reference
Biersdorfer, J. “The Security of Cellular Connections.” The New York Times, The New York Times, 10 Aug. 2018, www.nytimes.com/2018/08/10/technology/personaltech/security-wifi-lte-data.html.
Biersdorfer, J. “Staying Safer on Public Networks.” The New York Times, The New York Times, 4 May 2018, www.nytimes.com/2018/05/04/technology/personaltech/staying-safer-on-public-networks.html.
Lecture, Week 13
Weekly Writing Assignment, Week 13
For this week’s Weekly Writing Assignment, add a comment to this post in memo format that describes what you have contributed to your team’s collaborative project. Include any writing drafts and/or research that you have done. This is a way to maintain accountability for each team member’s contributions and to keep Prof. Ellis apprised of the work that your team members are doing to help bring the project together. Watch this week’s lecture for more details.
Instruction Manual Project of Upgrading To windows 10 in a Business/ University Settings
My instruction manual for upgrading to windows 10 in a business/ university settings can be found online here
Instruction Manual on Creating a Website for Beginners
The link to find the instruction manual for creating a website is found here.
1000 word expanded definition
New York City Technical College Department of Business
TO: Prof. Ellis
FROM: [ Shemei John]
DATE: 9/29/2021
SUBJECT: Expanded Definition Term: [Transhumanism]
[Introduction]
The intent of this memo is to introduce and inform technological Terminology we may or may not be fully familiar with. Terms such as “Networks”, “the internet of things”, “information technology”, “information sciences”, “data”, “transhumanism”, “hive-mind concept” and “Artificial Intelligence”. After careful consideration, I decided to research the term “Transhumanism”. Although, according to its popularity, the term isn’t mentioned a lot in today’s topics regarding technology, I do find it to be fascinating since it deals with the ideology that Mankind will transcend our current limitations through the use of technology. There are several sources I am considering for this topic to convey the definitions. So, I am going to include the definition of the word and its origins, throughout its history, from the Oxford etymology, and also from an excerpt taken from the books, “New bottles for new wine”, on Transhumanism, which discusses the ideology behind the term and its definition today.
[Definitions]
The Oxford English dictionary’s definition of transhumanism (n), is a deviation of the English word, transhuman, with the prefix “trans” meaning beyond or across the farther side of. The term was first used by Julian Huxley in his book “New bottles for new wine (1957)” in which he said, “The human species can..transcend itself..in its entirety, as humanity. We need a name for this belief. Perhaps transhumanism will serve: man remaining man, but transcending himself, by realizing new possibilities of and for his human nature.” [1] What Huxley is saying is, the belief in the will to surpass our current nature as humans is transhumanism. The term has surfaced occasionally in its etymology, being used again by Tom Bell, in his writings from “Extropy”, in which he says that the alternative to religion would be transhumanism. The term also has a definition more relevant the modernity of time.
[Context]
Over the course of its history from when it was first coined to current times, the word transhumanism has variated into slight nuances. Huxley’s definition of transhumanism is the belief that humankind will transcend our nature, but he was speaking specifically about the beliefs. He believed that either synchronously, or not, humans will consciously give rise to this belief in order to evolve. Today the word has slightly a different definition which includes some addition to it. [2] The definition today is familiarly used in science fiction. So, the current definition of the 21st century would be that, transhumanism is the belief that one day humankind with transcend our current limitations, ultimately achieving immortality, by use of science and technology.
I checked in the Oxford dictionary of science-fiction for some comparison. The word transhuman references with two other words, “cyborg” and “posthuman”. The definition of a transhuman according to the science fiction definition, [3]“someone whose body or mind has been transformed (e.g. by cyborgization or genetic engineering) so greatly that they are no longer considered human, especially one who now possesses greater abilities than normal humans.”
The term is more relevant today since we marvel at our current level of technology. This definition is what most of us are familiar with. We put a lot of our faith in technology. It has embedded its way into our lives. As I stated earlier, trans, the prefix, means beyond or across the farther side of, however, the suffix ‘ism’, usually accompany a verb, and means or implied an action that was or is to be performed, or a state of being, (Like Buddhism or Plagiarism). This definition is on par with current events.
Professor M. Battle-Fisher, in his article, “Transhuman, posthuman and complex humanness in the 21st century”, defines Transhumanism as the philosophy that you are already posthuman once you remove the current limitations of the current human being, “…the present state of our bodies.” Any kind of capacity that can enhance our abilities beyond our current state of flesh is transhumanism. He also states in the article that the only way to do that on the horizon is through the use of technology.
[1] Julian Huxley, New Bottles for New wine (page 17), Harper and Brothers publishing, 1957
[2] C. Christopher Hook, Transhumanism and Posthumanism, Encyclopedia of Bioethics(Vol. 5. 3rd ed.) Page 2517, Gale Publishing, 2004
[3][Oxford reference] Jeff Prucher, The Oxford Dictionary of Science Fiction, (Version 2007),
Oxford University Press, published 2006
[4] M. Battle-Fisher, Transhuman, posthuman and complex humanness in the 21st century, Science Direct, library.citytech.cuny.edu, 25 March 2019
[5]”Transhumanism,” in Oxford English Dictionary, 2nd ed. Oxford, UK: Oxford Univ. Press, Oct 6, def. 1. [Online]. Available: https://www.oed.com



