TO: Prof. Jason Ellis
FROM: Kanak Das
DATE: 12/01/2021
SUBJECT: 1500 word instruction manual on Secure Computer network/Wireless
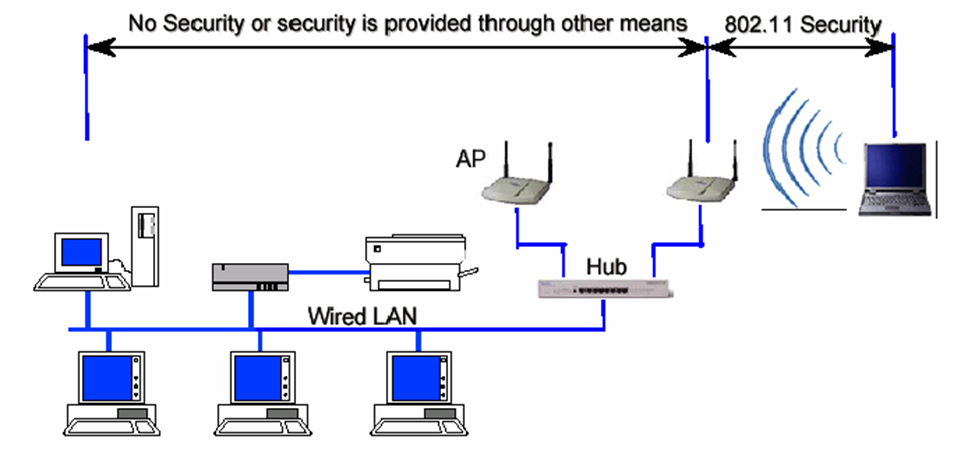
Encryption is one of the major subject to talk about in wireless security, Because, all wireless computers are radio transmitters and receivers, anyone can listen to the information that are being transfer or received, that’s why it’s important to have encryption enable on wireless network. So, that way even if the other people hear about the information, they would not be able to see the information. Only people will have access are the ones with proper passwords or proper wireless configuration.
Another major topic in wireless network is Hacking. For example, if you connect to public network, it can be easily intercepted by cybercriminal, where your personal data could be at risk. Whenever there is free public wi-fi, once you connect to these fake network everything you do online is monitor by cybercriminal. Who can scan your activity such as social media log in information. Cybercriminal can even easily transfer viruses, or other unnecessary software to your computer. That can cause serious damage to your computer and can get through your personal information.
Despite the fact these public networks can be harmful, there are ways to stay safe on public wi-fi. such as:
- Verify your connections, be sure to ask an employee what the actual public Wi-Fi is, in order to avoid fake network.
- Avoid checking sensitive or personal data, unless it’s necessary, avoid logging in Facebook, email and more importantly financial accounts while on public Wi-fi.
- Turn off Sharing, In your computer or the social media you are using there’s Sharing ON and OFF option. Turned that off while you are on public network.
- Turn your Wi-Fi off when you are done with your work. That can prevent falling your personal files and information on wrong hand.
So, now that there are some disadvantages of wireless security, it needs of improvement of protecting wireless data while they are in transit between a client and wireless access point.
- Techniques and Technology can be applied are:
- Use dynamic encryption key.
- Include real authentication key.
- Use strong encryption.
- Use improved cryptographic integrity protection for data frames.
- Improve session initiation.
- Use Strong Passwords.
- Have your Email connected to trusted device.
Another security technique can be applied is WPA which is Wi-fi Protected Access. WPA improve security by adding authentication Protocol for access control. It ensures the secure wireless communication. WPA support for temporal key integrity protocol TK IP which can be implemented in software with just firmware update. Along with that it also provides integrity checking using MIC, which is Message Integrity Code.
Configuring DNS on Windows, because The Domain Name System (DNS) is the protocol that makes the Internet usable by allowing the use of domain names. Its one of the safe zone to configure files or extract file.
Open the Server Manager from the task bar.
Click on DNS/ Right Click your server / select DNS Manger/ Click the Action Tab/ Select Configure a DNS Server.
-Select Configure a DNS Server in Windows Server 2012
The Configure DNS Server Wizard will come up click Next to continue and select one of the following actions:
– Create a forward lookup zone
A forward lookup zone is a DNS function that takes a domain name and resolves it to an IP address.
– Create forward and reverse lookup zones
A reverse lookup zone is a DNS function that takes an IP address and resolves it to a domain name.
– Configure root hints only
Root hints only Will have the IP addresses of DNS servers where records can be acquired.
This is the Configure DNS Server Wizard screen output in Windows Server 2012
Select where the DNS data will be maintained for your network resources, and then Click Next
Selecting a Primary Server location in Windows Server 2012
Enter your new zone name, in this case, your domain and Click Next.
This is the zone name insert field when configuring DNS in Windows Server 2012
Create a new zone file or use an existing one from a different DNS server
Creating a Zone file when configuring DNS in Windows Server 2012
Next you select how your server will respond to Dynamic Updates.
Select the do not allow Dynamic Updates option while Configuring DNS in Windows Server 2012
Select whether your DNS server should forward queries or not. If you choose YES, type the IP of the server and click Next. If NO, select No, it should not forward queries and Click Next.
Select one of the options to configure forwarders when Configuring DNS in Windows Server 2012
Click Finish and you’re all set.
Completing the DNS configuration in Window Server 2012
Furthermore, one of the case study I did, to learn this implementation even better is that there is Wi-Fi provider known as Web Titan. Web titan cloud for Wi-Fi is a web content filtering and network security solution for Wi-Fi providers. This is based in London UK. Selfridges ensure that guests and staff don’t have encounter malicious sites or view inappropriate content while using their Wi-Fi network.
According to this case study this is good Wi-Fi provider for business. Some of the reasons are, it provides a safer, faster and more secure environment for your hotspot guests and finally it allows you to control the content that you allow your guests to access. You can control multiple locations and routers And Web Titan Cloud handles any volume of usage. The product has extensive reporting, easily showing you usage and traffic. It also supports dynamic IPs and works with any device that joins your network. Another feature is that all of this protection and filtering comes without any compromise to speed.
Moreover, Security in public places has become one of the major issue in Wireless security field. There have been many references on how the problem can be fixed. Top of all that VPN also known as Virtual Private Network, can be one of the strongest ways to secure our Network. This is also can be called as Layer 3 security which left the IP network vulnerable to attacks. For instance, if you need to check sensitive data such your banking or any financial account while on public Wi-Fi use Virtual Private Network. Even if a cybercriminal positions himself in a middle of your connections, your data or files will be strongly encrypted.
In conclusion, securing wireless networks can be useful and difficult and harmful at the same time, but it all depends on how carefully we are using it. As I discussed on my previous paragraph there many techniques and method we apply in order to protect our privacy. There are procedure we can follow to help ourselves in wireless network, to ensure that a wireless network is as secure as possible, network administrator should follow several guidelines.
First, and most importantly the wireless network must be encrypted as I mentioned earlier. For this purpose, it is critical to use WPA based encryption rather than WEP based encryption. Since WEP encryption is severely flawed and can be cracked with free software in jut few minutes.
Second, it is important to remember that the benefits of wireless networking come up with price. To extend this idea more, data that are traveling over wired network, wireless data are much more exposed and open. Even, if wireless data are encrypted, the absence of physical wire network, it bring the hacker one step closer to gaining access to sensitive data.
Finally, a long password should be used for network authentication. The use of very strong password may be inconvenient or bothering for users, but it will help to prevent the hacker from foiling any password cracking attack. As you can see, the use of wireless network can be very beneficial and unfavorable at the same time but it is our choice how we are going to use it for, when to use it and have pick the right moment to value our wireless technology. Technology has changed a lot throughout the years, we don’t know what the technology hold for us in future. But the way our technology growing rapidly it won’t very long until we see something amazing on technology world. Network wireless has improved a lot through the years and surely it will be even better and safer with strong encryption and protected devices, where people can access network and Wi-Fi without any worry or hesitations.



