My instruction manual on How to Explore Ohm’s Law using MATLAB can be found online here.
Category: 1500-Word Instruction Manual
Instruction manual on how to counteract negative police interactions with the LAPD
Jun Gao
Professor Ellis
ENG 2575
Dec 5, 2021
Problem
In modern society, several pertinent ethical debates concerning the behaviors and practices of law enforcement agencies have positioned themselves at the forefront of our socio-political discourse. The ethical standards of several police departments in Los Angeles have been denoted towards a negative connotation in the eyes of its surrounding communities; a multitude of citizens from areas with diverse cultural demographics have been publicly oppressed in their neighborhoods through methods of over-policing, brutality, and other aggressive tactics that have manipulated the consensus on the topic of police for many individuals. There has been a considerable lack of consequence or reprimanding for many of the cases surrounding these malicious circumstances, coupled with a unique sense of inaction regarding the much-required institutional adaptations needed for Los Angeles-based policing systems. L.A.’s police system requires a substantial transformation from its current community-policing tactics to develop a considerably healthier dynamic between law enforcement and civilians, simultaneously investing in community-outreach initiatives, positive communication tactics, and abolishing unscrupulous police practices.
Background
The Los Angeles Police department is recognized globally for its capacity to abuse its operational powers and systematically oppressed communities of color. The agency is infamous for instigating many violent altercations between law enforcement and civilians, engaging in aggressive behavior often leading to physically violent (and sometimes fatal) disputes to occur. The Los Angeles Police Department’s actions dissolve any possibilities of a positive relationship between themselves and the communities they serve. Immediately following the effects of quarantine, the summer saw a substantial rise in social activist initiatives in direct response to community retaliation against police brutality on a nationwide scale. Reports described the events surrounding waves of policy-oriented violence as a “reign of terror,” citing multiple shootings of unarmed civilians, aggressive interactions between civilians and officers, and the escalation of social conflicts that lead to prevalent tension between the two parties. This notion has led to a stark dichotomy between the LAPD and the members of its various communities, demonstrating the adverse effects that malicious police operations had led to. “Police leaders have put forward accounts of each killing that they say to justify the use of force. But civil rights activists and victims’ families say the repeated bloodshed is a sign that police continue to escalate conflicts and resort to violence, even in the most routine of encounters – and that a more radical response is needed to prevent the next tragedy… LASD is the largest county police agency in the U.S., with jurisdiction in nearly 200 different towns and cities, and has a track record of brutality and controversial killings, racial profiling and corruption cases.”. (Levin, 3). The policing system in Los Angeles has been associated within the context of its direct altercation switch with the general public. The killing of unarmed civilians and the strong sense of conflict between both sides of the dichotomy has fueled a considerably virulent relationship based upon the seemingly repeating actions used to solve issues inadequately and efficiently de-escalate ambivalence.
Potential Methods of Solution Tactics
The assistance required to deal with the issues at hand is extensive. The nature of this problem is rooted in the standardization of aggressive methodologies being at the root of police training and the manipulation of community relations with law enforcement to be allocated towards destructive actions. Understanding empathy and utilizing the concept in community relations with the people(s) afflicted the most is crucial to comprehend the nature of police-community interactions. Many of these neighborhoods are actively disinterested in developing a healthy dialogue with police and incentivize the lack of nutritional communication standards to continue this dangerous narrative. “Racial and gender disparities abound within the criminal justice system and beyond. Many of these communities are made up of low-income neighborhoods with diverse racial demographics and a high percentage of black and Hispanic individuals, disproportionately affecting the livelihoods of minorities in Los Angeles. Males of color make up an unsettling majority of those stopped, arrested, and convicted of violent crimes in major cities all over America. They are also the majority of violent crime victims and are far more likely to be subjected to police force…Policing does not exist in a vacuum. It is a reflection of a country rife with racial disparity, which must be addressed in employment, healthcare, housing, education, and beyond.”. (Moore, 2-4). The correlation between race and police aggression is a necessary factor to consider when discerning the root of the attitudes taken when dealing with minorities from the responsibilities held by law enforcement officers—having a clear understanding of this dynamic and its subsequent issues coupled with the context of the historical relations between the two have to be analyzed to fully grasp the nature of the problem and any potential solutions in the attempt. Local political initiatives have been incentivized and propagated in recent times due to social backlash and numerous outcries for community legislators to create viable solutions to the issue. However, adequate assistance and community outreach programs must be invested if the point of de-escalation and the development of cordial, healthy communication tactics are created.
Survey
A survey would be conducted under the context of analyzing to dismantle oppressive practices of police aggression and the use of violent tactics in various communities with a particular area of interest in establishing relatively healthy methods of communication and interaction from the perspectives of both sides. Surveys in the form of questionnaires will be distributed to communities with the most active police presence in Los Angeles. Prevalent communities such as Skid Row, South LA, Lincoln Heights, and Hyde Park (neighborhoods with high crimes rates and heavy, active police presence) to gauge the public consensus on police-civilian relations to apply a relevant methodology in seeking for solutions to create better forms of communication between members of communities afflicted with prevalent police interaction. This would consequently allow law enforcement or create foundational grassroots initiatives to connect with community members on a more substantial basis, counteracting the negative ramifications of police-community tensions and creating a more equitable ecosystem for positive relationships to develop adequately.
Possible Solutions
Several viable solutions could potentially amend the toxic relationship between civilians and law enforcement in Los Angeles. The very root of the problem stems from critical factors that influence the trajectory of developing relations between both parties; excessive use of physical and lethal force, racial prejudice and discriminatory practices, and a stark lack of accountable consequences issued towards infringed actions are essential concepts of interests concerning the issue of police brutality and police-neighborhood interactions. The problems afflicting these areas can be derived from these three components, allocating their importance to the most significant concern and directing a focused objective towards establishing a solid foundation for new operations.
A foundational option for both police officers and Los Angeles residents to consider would be participating in community relations programs and reforming the entire law enforcement training process to be geared towards empathetic dialogue and practical de-escalation education to standardize the use of acceptable conflict resolution practice and to build a sense of trust among Los Angeles communities and their police department(s). The use of educational programs for police departments (and communities) would effectively solve many of these operational misconceptions and faulty practices in the currently abusive institution. Organizations dedicated to teaching police officers about the core concepts concerning healthy police de-escalation tactics should implement their techniques in Los Angeles to create a status quo for beneficial, efficient policing tactics to be implemented into educational routines. “Programs to improve police-community relations benefit the community by decreasing fear and stress, especially in a community where the presence of law enforcement increases the anxiety of its citizens. A decrease in this anxiety can regulate potential conflict before it begins…These programs to improve police-community relations can benefit police departments by decreasing or de-escalating conflicts that may garner negative consequences, keeping law enforcement and the community in what may seem like an ongoing battle.”. (Police Peacekeeping, 2-4). Programs and networks that encourage officers to resort to “tactical communication skills” (skills used for high-stress and dangerous altercations) and conflict resolution will drastically reduce the apparent need for physical force to be applied during quarrels, and lead to an overall increase in policing efficiency and interpersonal community relations. One study found that “a single instance of positive contact with a uniformed police officer can substantially improve public attitudes toward police, including legitimacy and willingness to cooperate.” (Peyton, 1); this information directly correlates to the notion that creating avenues for these positive interactions to occur through education and congregation will effectively lead to beneficial results.
Conclusion
The nature of police-neighborhood relation is a topic that polarizes opinion. Aggressive acts stemming from non-communicative situations with police officers and (innocent) civilians have developed a sense of tension between both groups, leading to a less-than-favorable dynamic held between members of this evil dichotomy. Active Los Angeles communities must initiate resistance against the normalization of these practices on social and political platforms to dismantle oppressive practices systematically, and violent behaviors carried out by members of a corrupt police force.
Works Cited
Peyton, K., Sierra-Arévalo, M., & Rand, D. G. (2019). A field experiment on community policing and police legitimacy. Proceedings of the National Academy of Sciences, 116(40), 19894-19898.
ACLU. (n.d.). Fighting police abuse: A community action manual. American Civil Liberties Union. https://www.aclu.org/other/fighting-police-abuse-community-action-manual.
Levin, S. (2020, September 6). ‘Reign of TERROR’: A summer of police violence in Los Angeles. The Guardian. https://www.theguardian.com/us-news/2020/sep/06/los-angeles-police-killings-dijon-kizzee-andres-guardado.
Chang, A. (2020, June 5). LA’s history of racial tensions and Police Brutality, Revisited. NPR. https://www.npr.org/2020/06/05/871083491/las-history-of-racial-tensions-and-police-brutality-revisited.
Moore, M. (2021, June 3). Chief Michel Moore: Inequities in policing are a reflection of a racially biased society. Los Angeles Times. https://www.latimes.com/opinion/story/2021-06-03/chief-michel-moore-racially-biased-policing.
N/A. (2021, March 3). Programs to improve POLICE-COMMUNITY RELATIONS: Pollack Peacebuilding. Pollack Peacebuilding Systems. https://pollackpeacebuilding.com/police-community-relations-programs/.
Instructional Manual for Creating a Webshare
My instruction manual for Instructional Manual for Creating a Webshare can be found online here
Instruction Manual For Getting Started With Object-Oriented Programming
My instruction manual for Getting Started With Object-Oriented Programming can be found online here
Instruction Manual Project for Installing and Configuring a VirtualBox Machine
My instruction manual for Installing and Configuring a VirtualBox Machine can be found online here
1500 Word Instruction manual
My Instruction maual for Instruction manual for Secure Computer network/Wireless/IIS web server/Share files is HERE
Instruction Manual on how to hack your Nintendo 3DS system
To: Prof Jason Ellis
From: Shemei John
Date: 11/17/2021
Subject: A Nintendo 3DS hack Guide
[1.0 Introduction]
This is a guide to modify your Nintendo 3DS system with custom firmware in order to personalize and customize the device. The perks of having a custom firmware are developer level and administrative level skills and access to a system, giving you more control of the devices potential capabilities, by unrestricting certain features, or accessing them otherwise. The then unrestricted firmware gives you access to custom software, applications and software themes created by others on the internet. This is for creative purposes, since you can create and install your own apps and features, as well. There are several methods to achieve this. I will be using the one most familiar to me.
[1.1 Purpose]
The purpose of this instruction manual is to practice and demonstrate administrative techniques that are familiar with Computer Information Systems. While there are a few methods to achieve this, this manual’s purpose is to also convey and explain what is being done. Popular uses for custom firmware include:
- Bypassing the region lock, allowing you to play games from other regions
- Home menu customization, using community-created themes and badges
- Modification of games (“ROM hacks”) through LayeredFS
- Save data editing, backup, and restore
- Emulation of older consoles, as well as native playback of DS and GBA games
- Installing your physical cartridges for digital use
[1.2 Intended Audience]
This manual is intended for anyone who own a Nintendo 3DS system or any student who declares a Computer Information Systems major, and are looking for practical experience learning about a computer system. It is similar to any computers system.
[1.3 Scope]
The scope of this mission is to download and install custom firmware on a stock or factory Nintendo 3DS system and proceed by performing specific functions to unlock and access restricted functions of the 3DS.
[1.4 Safety and Disclaimers]
Whenever performing any restricted tasks of any kind on any computing device there are always risks involve. It is imperative that you read and follow this manual correctly to minimize the chances of bricking.
“Bricking” is a terminology used by the computer community. Bricking means the device becomes unusable after a software, or more specifically, a firmware update was not successful. For example, the device powers on but the screen is blank and the Operating System doesn’t load. Now whenever you turn on the device the lights are on, but the screen is off forever! The risks of bricking your 3DS device has been reduced over the years significantly but there is still a chance of it happening even when you do everything correctly. This can be because of the custom firmware that was edited by others. Please be aware that you are attempting this at your own risk of bricking or voiding any warranty you may still have on your device by titivating with it. Also please be aware that since this gains restricted access to the system’s capabilities, if you attempt this method to download illegal games you could be banned from it’s network features or punished even worse.
[2.0 List of Materials and Equipment Needed]
- Computer device [a laptop is fine]
- Micro SD card reader for your computer device
- Micro SD card with at least 8G [I recommend more if you’ll need space to install more data, like downloading soft copy games. I have a 32G]
- Any unmodified Nintendo 3DS, 3DS XL, 3DS LL, 2DS system, with system firmware version of 1.0.0 – 11.3.0, anything higher will need a different method than the one in this instructional manual.
- A #00 cross-head (+) should do for the Nintendo 3DS, Nintendo 3DS XL, and Nintendo 2DS, to open up the back panel to retrieve Micro SD card.
[3.0 Directions]
[3.1] Prep devices. Check and make sure your device is compatible with this method before attempting. Make sure your devices are fully charged while performing tasks.
- Turn off your Nintendo System device and expose the Micro SD card located inside by removing the back panel screws with the mini cross head screwdriver. The screws are attached to the panel itself so be careful not to break it.
- Remove the Micro SD card and mount it to your computer
- Open the root folder of the SD card on your computer. The root folder is the main folder, or first folder of the device.
- Create a separate folder on your desktop and copy the root folder on your Micro SD card to the newly created folder on your desktop. Backing up your data before performing any kind of work on a computer is a Computer specialists’ bread and butter.
- You will then need to format your SD card to FAT32/MBR
[3.2] Acquiring boot9strap via soundhax. This is the easiest way to hack the system. Download these files from the internet. You can find them anywhere, just make sure it is the latest version. I use Github since it’s a peer-peer sharing website by users like you and I.
- Create an additional folder called boot9strap and download and extract files here
- I suggest you create a folder for each to avoid any confusion of files
- Download the latest release of SafeB9SInstaller
- Download the latest release of boot9strap
- Download the latest release of Luma3DS
- Download the latest release of universal-otherapp
[3.3] Open up your folder containing the boot9strap files and located each of the following:
- Copy the Soundhax .m4a to the root of your SD card
- Copy otherapp.bin to the root of your SD card
- Copy boot.firm and boot.3dsx from the Luma3DS .zip to the root of your SD card
[3.4] Create a folder named boot9strap on the root of your SD card. The root of the SD card is the area that the root folder is located in. Basically, the SD card itself.
- Copy boot9strap.firm and boot9strap.firm.sha from the boot9strap .zip to the /boot9strap/ folder on your SD card
- Copy SafeB9SInstaller.bin from the SafeB9SInstaller .zip to the root of your SD card
[3.5] Reinsert your Micro SD card into your 3DS system and power it on
[3.6] After you power on your device, several applications should be visible in your library, install the boot9strap by:
- Launch Nintendo 3DS Sound
- Locate /SDCARD, then play “<3 nedwill 2016” This can take several tries to be patient. If the program freezes, soft reset but powering off your device using the power button and repeat. If your versions are 9.4.0, 9.5.0 or 9.6.0, and you experience this problem, you will need to sounhax using the homebrew launcher (Separate manual). Once successful, wait for all checks to complete then press the (A) button to reset device.
[3.7] After resetting the device should be in a Luma3DS configuration window. Configure Luma3DS by:
- Using the (A) and (D-pad) to maneuver the menu, highlight “NAND or user string in System Settings” and press (START) to save and reboot if you receive an error just continue
The system will now boot to the custom firmware (Luma3DS) by default as long as the SD card is inserted. Luma3DS does not look any different from the normal HOME menu. This instruction manual is demonstrate how to apply custom firmware to the 3DS. The 3DS is now unlocked you can install additional applications that vastly simplify the loading system of the firmware. Your Device can now load the custom firmware but only from the SD card. Some additional applications essential to the firmware that will be useful can now be installed and used, such as:
- FBI (installs CIA formatted games)
- Themely (installs custom themes)
- Luma3DS Updater (updates your CFW installation easily)
- GodMode9 (multipurpose tool which can do NAND and Cartridge functions)
These are all user created programs and files shared by the community. For instance, FBI can allows the user to install files directly to your SD card simply by scanning a QR code.
4.0 Glossary
Brick – The new or expensive device that no longer works turns into a simple paper weight. The computer community uses this term to describe the result of an action taken to cause a device to stop functioning, not physically, but by loss or corruption of firmware, that causes the device to stop working.
Emulation – A reproduction or function of computing program. Often used in the video game world for old video game consoles that are now considered so small they can be replicated on a computer laptop because they do not take up a lot of space.
Firmware – specialized software created specifically for a particular device. Firmware is similar to software, the only difference is that firmware is physically written into the hardware of the device. For this reason, firmware does not require the use of an operating system to function.
Boot9strap – This program installed on your SD card allows the system to run these applications free without the use of an emulation
NAND – A chip used to store the firmware of the system
Root – The SD card itself and not the folders that is already on it. When you open or mount your SD card, that visible area is the root. The root folder is the folder that is located in this area
Boot – A term that came from the term “bootstrap” or getting your first orders. Today it essentially means to turn on your device but to boot simply means to give your computer instructions to turn it on
Soundhax – This refers to the homebrew application. This exploit gives you entry to the homebrew application that this custom firmware is basically built on without any outside assistance.
7.0 Reference List
1500 word manual instruction on secure computer network/wireless
TO: Prof. Jason Ellis
FROM: Kanak Das
DATE: 12/01/2021
SUBJECT: 1500 word instruction manual on Secure Computer network/Wireless
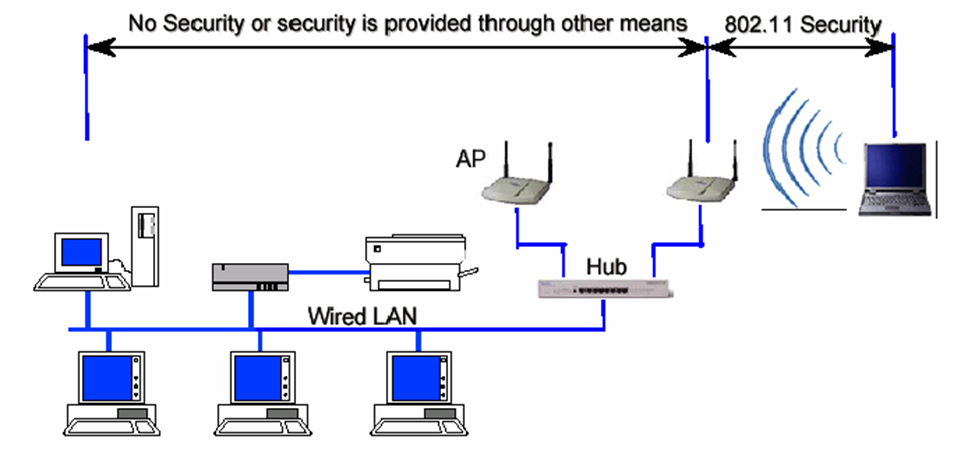
Encryption is one of the major subject to talk about in wireless security, Because, all wireless computers are radio transmitters and receivers, anyone can listen to the information that are being transfer or received, that’s why it’s important to have encryption enable on wireless network. So, that way even if the other people hear about the information, they would not be able to see the information. Only people will have access are the ones with proper passwords or proper wireless configuration.
Another major topic in wireless network is Hacking. For example, if you connect to public network, it can be easily intercepted by cybercriminal, where your personal data could be at risk. Whenever there is free public wi-fi, once you connect to these fake network everything you do online is monitor by cybercriminal. Who can scan your activity such as social media log in information. Cybercriminal can even easily transfer viruses, or other unnecessary software to your computer. That can cause serious damage to your computer and can get through your personal information.
Despite the fact these public networks can be harmful, there are ways to stay safe on public wi-fi. such as:
- Verify your connections, be sure to ask an employee what the actual public Wi-Fi is, in order to avoid fake network.
- Avoid checking sensitive or personal data, unless it’s necessary, avoid logging in Facebook, email and more importantly financial accounts while on public Wi-fi.
- Turn off Sharing, In your computer or the social media you are using there’s Sharing ON and OFF option. Turned that off while you are on public network.
- Turn your Wi-Fi off when you are done with your work. That can prevent falling your personal files and information on wrong hand.
So, now that there are some disadvantages of wireless security, it needs of improvement of protecting wireless data while they are in transit between a client and wireless access point.
- Techniques and Technology can be applied are:
- Use dynamic encryption key.
- Include real authentication key.
- Use strong encryption.
- Use improved cryptographic integrity protection for data frames.
- Improve session initiation.
- Use Strong Passwords.
- Have your Email connected to trusted device.
Another security technique can be applied is WPA which is Wi-fi Protected Access. WPA improve security by adding authentication Protocol for access control. It ensures the secure wireless communication. WPA support for temporal key integrity protocol TK IP which can be implemented in software with just firmware update. Along with that it also provides integrity checking using MIC, which is Message Integrity Code.
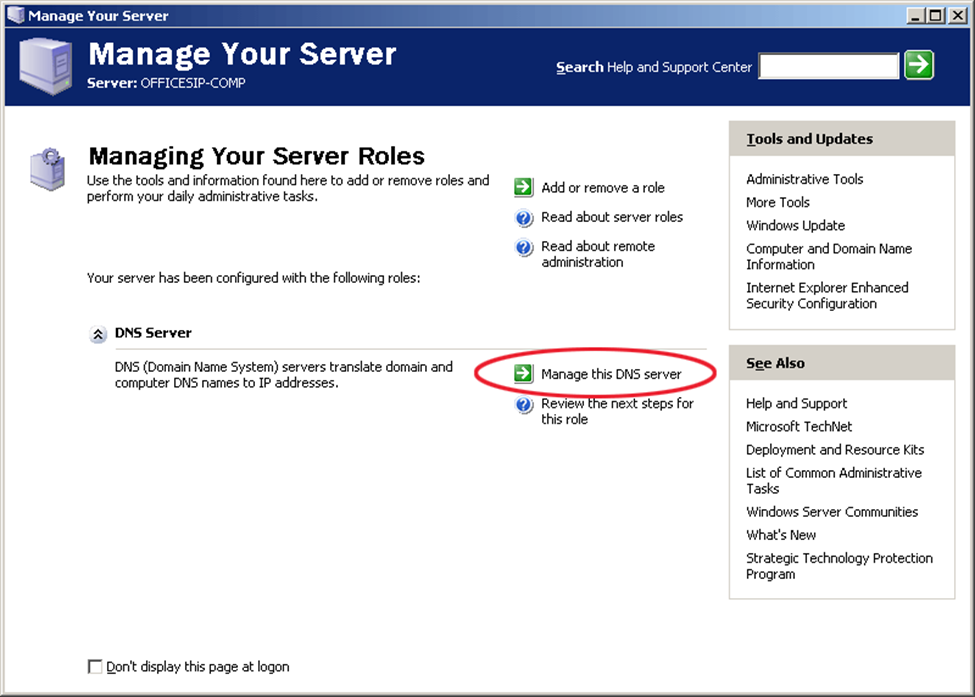
Configuring DNS on Windows, because The Domain Name System (DNS) is the protocol that makes the Internet usable by allowing the use of domain names. Its one of the safe zone to configure files or extract file.
Open the Server Manager from the task bar.
Click on DNS/ Right Click your server / select DNS Manger/ Click the Action Tab/ Select Configure a DNS Server.
-Select Configure a DNS Server in Windows Server 2012
The Configure DNS Server Wizard will come up click Next to continue and select one of the following actions:
– Create a forward lookup zone
A forward lookup zone is a DNS function that takes a domain name and resolves it to an IP address.
– Create forward and reverse lookup zones
A reverse lookup zone is a DNS function that takes an IP address and resolves it to a domain name.
– Configure root hints only
Root hints only Will have the IP addresses of DNS servers where records can be acquired.
This is the Configure DNS Server Wizard screen output in Windows Server 2012
Select where the DNS data will be maintained for your network resources, and then Click Next
Selecting a Primary Server location in Windows Server 2012
Enter your new zone name, in this case, your domain and Click Next.
This is the zone name insert field when configuring DNS in Windows Server 2012
Create a new zone file or use an existing one from a different DNS server
Creating a Zone file when configuring DNS in Windows Server 2012
Next you select how your server will respond to Dynamic Updates.
Select the do not allow Dynamic Updates option while Configuring DNS in Windows Server 2012
Select whether your DNS server should forward queries or not. If you choose YES, type the IP of the server and click Next. If NO, select No, it should not forward queries and Click Next.
Select one of the options to configure forwarders when Configuring DNS in Windows Server 2012
Click Finish and you’re all set.
Completing the DNS configuration in Window Server 2012
Furthermore, one of the case study I did, to learn this implementation even better is that there is Wi-Fi provider known as Web Titan. Web titan cloud for Wi-Fi is a web content filtering and network security solution for Wi-Fi providers. This is based in London UK. Selfridges ensure that guests and staff don’t have encounter malicious sites or view inappropriate content while using their Wi-Fi network.
According to this case study this is good Wi-Fi provider for business. Some of the reasons are, it provides a safer, faster and more secure environment for your hotspot guests and finally it allows you to control the content that you allow your guests to access. You can control multiple locations and routers And Web Titan Cloud handles any volume of usage. The product has extensive reporting, easily showing you usage and traffic. It also supports dynamic IPs and works with any device that joins your network. Another feature is that all of this protection and filtering comes without any compromise to speed.
Moreover, Security in public places has become one of the major issue in Wireless security field. There have been many references on how the problem can be fixed. Top of all that VPN also known as Virtual Private Network, can be one of the strongest ways to secure our Network. This is also can be called as Layer 3 security which left the IP network vulnerable to attacks. For instance, if you need to check sensitive data such your banking or any financial account while on public Wi-Fi use Virtual Private Network. Even if a cybercriminal positions himself in a middle of your connections, your data or files will be strongly encrypted.
In conclusion, securing wireless networks can be useful and difficult and harmful at the same time, but it all depends on how carefully we are using it. As I discussed on my previous paragraph there many techniques and method we apply in order to protect our privacy. There are procedure we can follow to help ourselves in wireless network, to ensure that a wireless network is as secure as possible, network administrator should follow several guidelines.
First, and most importantly the wireless network must be encrypted as I mentioned earlier. For this purpose, it is critical to use WPA based encryption rather than WEP based encryption. Since WEP encryption is severely flawed and can be cracked with free software in jut few minutes.
Second, it is important to remember that the benefits of wireless networking come up with price. To extend this idea more, data that are traveling over wired network, wireless data are much more exposed and open. Even, if wireless data are encrypted, the absence of physical wire network, it bring the hacker one step closer to gaining access to sensitive data.
Finally, a long password should be used for network authentication. The use of very strong password may be inconvenient or bothering for users, but it will help to prevent the hacker from foiling any password cracking attack. As you can see, the use of wireless network can be very beneficial and unfavorable at the same time but it is our choice how we are going to use it for, when to use it and have pick the right moment to value our wireless technology. Technology has changed a lot throughout the years, we don’t know what the technology hold for us in future. But the way our technology growing rapidly it won’t very long until we see something amazing on technology world. Network wireless has improved a lot through the years and surely it will be even better and safer with strong encryption and protected devices, where people can access network and Wi-Fi without any worry or hesitations.
Instruction Manual Project of Upgrading To windows 10 in a Business/ University Settings
My instruction manual for upgrading to windows 10 in a business/ university settings can be found online here
Instruction Manual for Installing an Android Emulator.
My instruction manual for installing an android emulator can be found online here.



