Instruction Manual Project
This week, you will want to reply all to the email that I send to each team for peer review of your instruction manuals. Pay attention to the names in your email, because I have reassigned some students to different teams due to some teams losing members. If you see a new name in your team, please welcome that person, and if you are a new member to a team, please introduce yourself to your new teammates.
As discussed in today’s lecture, here is an example of an instruction manual for your final layout before circulating in peer review.
Collaborative, Team-Based Project
While we are wrapping up your individual Instruction Manual projects, we are going to begin working on your Collaborative, Team-Based Project so that you have as much time as possible to complete this important set of interconnected assignments that will carry us to the end of the semester.
Below, I have mapped out the Collaborative, Team-Based Project diagrammatically.
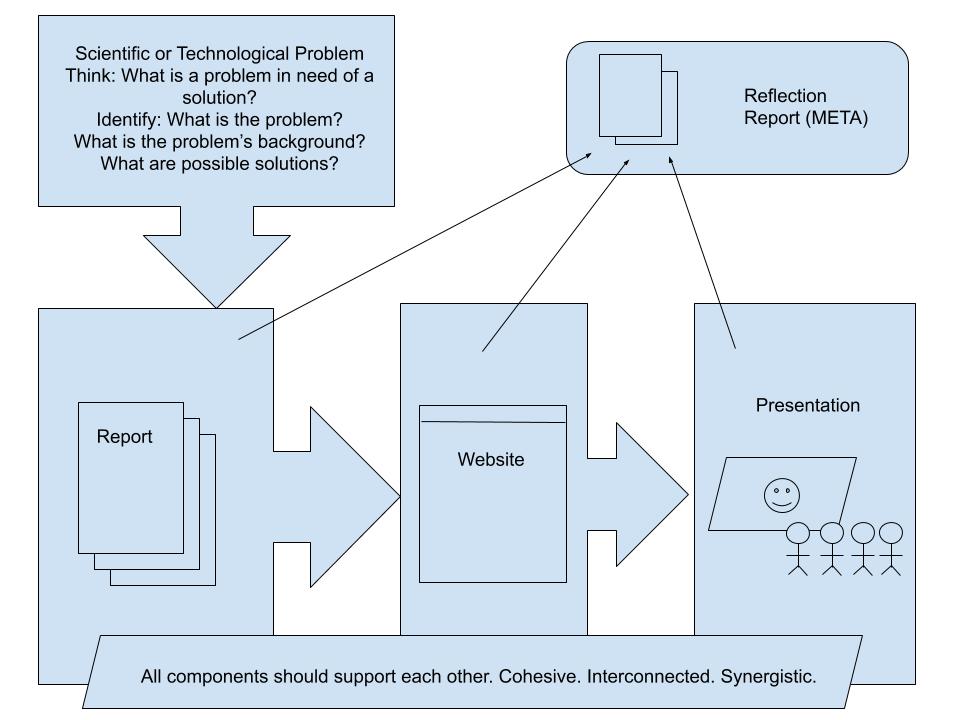
The Collaborative, Team-Based Project is comprised of these assignments:
- Collaborative: 4000-6000-Word Analytical Research Report, 15%
- Each team member contributes 1000-1500-word contribution to a 4000-6000-word analytical research report on a scientific or technological problem that demonstrates: 1) knowledge of the history and context of the problem, 2) knowledge of the causes and nature of the problem, 3) ideas for solving the problem, 4) the ability to explain the problem and offer possible solutions to a general audience, 5) the ability to integrate written work with the written work of a partner or partners in a coherent report, and 6) knowledge of proper research report format. At least six library-sourced citations must be included (non-library-sourced citations are encouraged, but they do not count toward the six library-sourced sources). Any outside sources cited should be documented according to APA format.
- Collaborative: Seven-to-Ten-Minute Oral Analytical Research Report on a Scientific or Technological Problem, 10%
- The goal of this part of the project is to transform your written report into an spoken presentation anchored by a PowerPoint or other visual presentation supplement. As a team, adapt and present your analytical research report as an oral presentation that demonstrates: 1) knowledge of oral presentation techniques and conventions, 2) the ability to organize a presentation effectively, 3) the ability to incorporate various media into the presentation, including appropriate computer software, 4) awareness of audience, 5) the ability to communicate the value of the product or service in clear spoken English, 6) the ability to answer audience questions, 7) the ability to collaborate productively with a partner or partners, and 8) the ability to explain the problem and offer possible solutions to a general audience.
- Collaborative: Website Advertising a Product or Service Responding to the Analytical Research Report and Oral Presentation, 10%
- The goal of this part of the collaborative project is to imagine a service or product that your team can offer that is related to your research report and oral presentation, both of which will be featured on the website in some way. The website should demonstrate: 1) knowledge of the product or service offered, of pertinent market forces, and of the potential customer base, 2) basic knowledge of web page design and composition, including appropriate software. The website will be based on your presentation and it is encouraged to be integrated into your presentation (perhaps to demonstrate how your team is promoting your product or service). All graphics, logos, design, and text must be created by your team.
- Individual: 250-500-Word Reflection on Collaboration, 5%
- At the end of the collaborative project, each student will have an opportunity to submit their own 250-500-word Reflection on Collaboration directly to Prof. Ellis via email. This document should include a discussion of challenges faced and overcome (or not) by the team, their contribution to the project, and the contribution of their teammates to the project. The instructor will consider these documents when assigning grades on the collaborative project.
The main part of the collaborative project is the research report. It anchors everything else. It should be completed first and adapted or transformed for use in the other deliverables: the website and the presentation. The report, website, and presentation will be submitted on our OpenLab Course Site. You will find the work done on earlier projects, such as article summarization, defining terms, and using proper citation formats, will all be in play on this project.
Each team member should keep a log in their notebook about the work that they contribute to the project as well as their observations about other team members’ contributions. These notes will inform an individual report that each team member will submit directly to Prof. Ellis via email as the Reflection on Collaboration.
Think of each of the following projects as part of an interconnected larger project. Each team member should contribute to each part, but individual team members may take the lead on one part versus the others depending on their skill set and interests. For example, one team member may take the lead on the research report and collect contributions from the other team members for the first draft, and another team member may take the lead on the presentation or the website.




