If you couldn’t make it to the Literary Arts Festival last week but would like to earn the extra credit, you may watch the ~2 hour long event video above, write 250-words about your experience (who did you hear speak? whose work resonated with you? what did you take away from the event?), and email your response to Prof. Ellis (jellis at citytech.cuny.edu).
Richard Rivera’s Instructional Manual for Building a Personal AMD Gaming Computer
For this project, I wrote an instruction manual for building a personal AMD gaming computer.
Angela Hernandez’s Instructional Manual for Getting Started with Git and GitHub
For this project, I wrote an instructional manual for getting started with Git and GitHub.
Lecture, Week 10
In addition the Google Drive folder detailed in this week’s Weekly Writing Assignment below, you should create a second Google Doc within that shared folder that you will use for writing your Research Report. It can also be used to collect your notes, research, and reference entries. Be sure to document all of your research so that quotes are properly quoted and given parenthetical citations and a bibliographic entry in APA format is added to the References list at the end. You can copy the following outline into this document as a guide for the general layout of your Research Report:
Introduction (topic and why your report is important) Objectives of the research (what were you attempting to do?) Method (methodology–what kinds of research did you do, how did you do it, and why is the research sound?) Results (what did you find in your research? facts, quotes, figures, interviews, surveys, etc.) Discussion (how do you interpret your results? what story does your data tell us? results and discussion can be combined, but title this section appropriately if you do so) Conclusions (what conclusions do you draw from your results and discussion? what is the significance of what you discovered?) Recommendations (what do you think should be done to solve the research problem based on your research? this section is what all of your work is leading up to.) References
Also, here are some resources and examples that I discussed in this week’s lecture to help you with writing and designing your analytical research report.
- Doodle (for finding meeting times for your team)
- Explanations of report parts (look under Primary Research Report, but remember you are writing a secondary research report)
- Example: Issues with Quantum Computing
- Example: Research Report on 5G
- Sample Research Report (note the layout and design)
Weekly Writing Assignment, Week 10
After watching this week’s lecture, your team should do the following:
- Establish another communication channel for team discussion besides email (you may use email, but you should have another channel that supports easier and faster communication among the team members).
- Discuss and decide amongst yourself which project your team chooses from last week’s brainstorming exercise.
- Create a shared folder on Google Drive and add all team members to the folder as Editors
- One team member should create a Google Doc in the shared folder. In this document, write a brief memo with TO (Prof. Ellis), FROM (all team members’ first and last names), DATE, SUBJECT (Collaborative Project Topic). In the content area, write a few sentences describing the scientific or technical problem that you will research for your collaborative project. Include any information about how your deliberations and discussion might have focused your topic from what one of your team members’ presented in the brainstorming exercise.
- Each team member should copy-and-paste your completed memo into a comment made to this Weekly Writing Assignment post. This demonstrates that all team members can access your shared Google Drive folder and its files.
For this week’s homework, you should discuss how to begin your research. Perhaps delegate one resource to each team member to find a few possible sources each. For example, one team member should look in IEEExplore, one team member should look in Academic Search Complete, etc. for library-based resources, including also General OneFile (Gale), Ebook Central, and others here.
Lecture, Week 9
Instruction Manual Project
This week, you will want to reply all to the email that I send to each team for peer review of your instruction manuals. Pay attention to the names in your email, because I have reassigned some students to different teams due to some teams losing members. If you see a new name in your team, please welcome that person, and if you are a new member to a team, please introduce yourself to your new teammates.
As discussed in today’s lecture, here is an example of an instruction manual for your final layout before circulating in peer review.
Collaborative, Team-Based Project
While we are wrapping up your individual Instruction Manual projects, we are going to begin working on your Collaborative, Team-Based Project so that you have as much time as possible to complete this important set of interconnected assignments that will carry us to the end of the semester.
Below, I have mapped out the Collaborative, Team-Based Project diagrammatically.
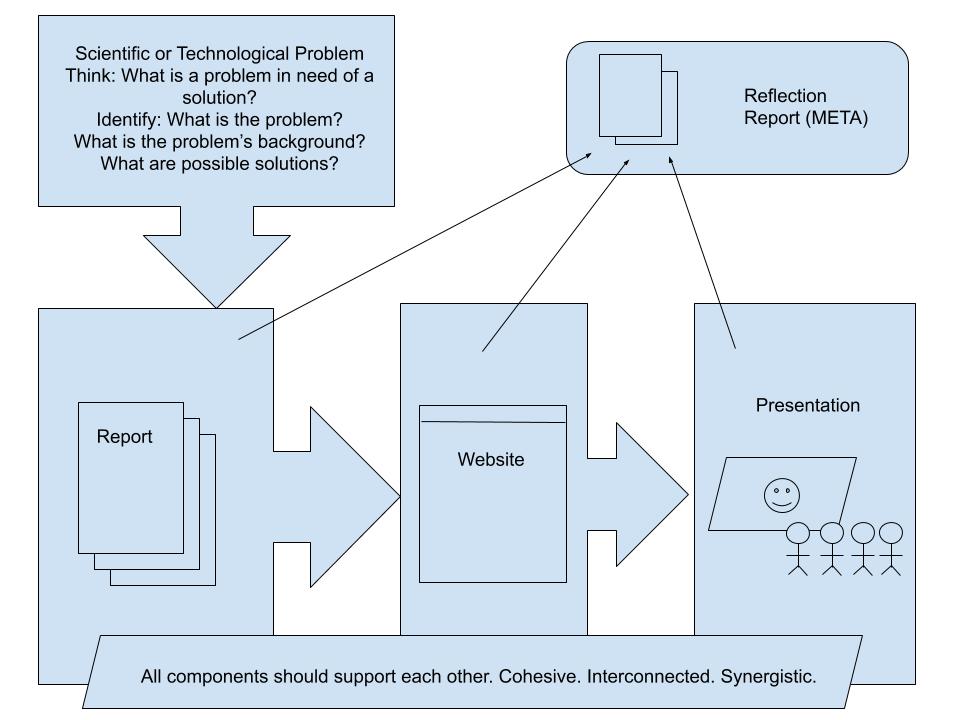
The Collaborative, Team-Based Project is comprised of these assignments:
- Collaborative: 4000-6000-Word Analytical Research Report, 15%
- Each team member contributes 1000-1500-word contribution to a 4000-6000-word analytical research report on a scientific or technological problem that demonstrates: 1) knowledge of the history and context of the problem, 2) knowledge of the causes and nature of the problem, 3) ideas for solving the problem, 4) the ability to explain the problem and offer possible solutions to a general audience, 5) the ability to integrate written work with the written work of a partner or partners in a coherent report, and 6) knowledge of proper research report format. At least six library-sourced citations must be included (non-library-sourced citations are encouraged, but they do not count toward the six library-sourced sources). Any outside sources cited should be documented according to APA format.
- Collaborative: Seven-to-Ten-Minute Oral Analytical Research Report on a Scientific or Technological Problem, 10%
- The goal of this part of the project is to transform your written report into an spoken presentation anchored by a PowerPoint or other visual presentation supplement. As a team, adapt and present your analytical research report as an oral presentation that demonstrates: 1) knowledge of oral presentation techniques and conventions, 2) the ability to organize a presentation effectively, 3) the ability to incorporate various media into the presentation, including appropriate computer software, 4) awareness of audience, 5) the ability to communicate the value of the product or service in clear spoken English, 6) the ability to answer audience questions, 7) the ability to collaborate productively with a partner or partners, and 8) the ability to explain the problem and offer possible solutions to a general audience.
- Collaborative: Website Advertising a Product or Service Responding to the Analytical Research Report and Oral Presentation, 10%
- The goal of this part of the collaborative project is to imagine a service or product that your team can offer that is related to your research report and oral presentation, both of which will be featured on the website in some way. The website should demonstrate: 1) knowledge of the product or service offered, of pertinent market forces, and of the potential customer base, 2) basic knowledge of web page design and composition, including appropriate software. The website will be based on your presentation and it is encouraged to be integrated into your presentation (perhaps to demonstrate how your team is promoting your product or service). All graphics, logos, design, and text must be created by your team.
- Individual: 250-500-Word Reflection on Collaboration, 5%
- At the end of the collaborative project, each student will have an opportunity to submit their own 250-500-word Reflection on Collaboration directly to Prof. Ellis via email. This document should include a discussion of challenges faced and overcome (or not) by the team, their contribution to the project, and the contribution of their teammates to the project. The instructor will consider these documents when assigning grades on the collaborative project.
The main part of the collaborative project is the research report. It anchors everything else. It should be completed first and adapted or transformed for use in the other deliverables: the website and the presentation. The report, website, and presentation will be submitted on our OpenLab Course Site. You will find the work done on earlier projects, such as article summarization, defining terms, and using proper citation formats, will all be in play on this project.
Each team member should keep a log in their notebook about the work that they contribute to the project as well as their observations about other team members’ contributions. These notes will inform an individual report that each team member will submit directly to Prof. Ellis via email as the Reflection on Collaboration.
Think of each of the following projects as part of an interconnected larger project. Each team member should contribute to each part, but individual team members may take the lead on one part versus the others depending on their skill set and interests. For example, one team member may take the lead on the research report and collect contributions from the other team members for the first draft, and another team member may take the lead on the presentation or the website.
Weekly Writing Assignment, Week 9
For this week’s Weekly Writing Assignment, I would like you to brainstorm some possible scientific or technical problems that you can discuss with your team. Specifically, I would like you to focus on scientific or technical problems related to your major and career goals. Perhaps it will involve problems relating to computing hardware or software, networking, electrical engineering challenges, applications of computing and networking to other real world problems (such as, smart power grids, driverless cars, Bitcoin energy use, etc.). There are many, many problems out there for you to think about, discuss, and choose among for your team’s project.
So, the Weekly Writing Assignment is to write at least 250-words in a memo format addressed to Prof. Ellis with the subject, “Team Project Brainstorming,” and discussing three possible technical or scientific problems relating in some way to your major and career goals. For each problem, clearly state what the problem is, who or what industry it affects, and some of your own thoughts about how the problem might be solvable. After you’ve written this memo, copy-and-paste it into a comment on this blog post AND circulate it via email (reply all) to the email that I will send to each team for peer review (on the Instruction Manual project).
Extra Credit: Literary Arts Festival

If you’d like to earn extra credit to apply toward a Weekly Writing Assignment or points to another assignment as needed, you can attend the Literary Arts Festival next week, write at least 250 words describing your experience of the event (naming the people you listened to, what you learned and liked, etc.), and email your event write-up to me at jellis at citytech.cuny.edu.
To attend the event, you will need to register at this website in advance to receive the Zoom Webinar link.
Mamadou Diallo’s Expanded definition of computer Network Simulation and Network Security Auditing in A Spatial Context of An Organization (CNSNSASCO)
To: Prof. Ellis
From: Mamadou Diallo
Date: 03/26/2021
SBJECT: Expanded definition of Computer Network simulation and Network security auditing in A Spatial Context of an Organization (CNSNSASCO)
Table of Contents
Introduction
Computer networking is the current mode of operation for most organizations today. The flow of information within and outside organizations is done using computer devices. The growing concern for the use of computer networking is data security and computer simulation. Some of the commonly used terms that address computer network security include Breach, firewall, and malware. A breach is a term used to refer to when a hacker has successfully accessed complete control of a computer device or a network. A Firewall is a software program that is put in place to prevent any corrupt or unauthorized access to a computer system or network. Finally, our main focus area, malware, refers to that malicious software that corrupts and destroys a computing device or network.
Definitions
The term malware is a broad description of specific malicious programs that include viruses, trojans, worms, and spyware(Bazrafshan et al., 2013). Although there is more malicious software affiliated with malware, we will focus on the four examples named above. The four are the most common types of malware that affect the network of an organization. Some of this malware can originate from within the organization, usually known as micro threats, or can come from outside the company, usually known as macro threats. Most of the macro threats come from competitors, government regulations, technological changes, and customer’s changes in taste and preferences. The micro threats originate from malicious persons inside the company or outside persons like hackers and crackers who might infect computer devices and networks with viruses, trojans, and worms.
Context
A computer virus is a malicious program that corrupts data in a computer. A computer virus, just like a human virus, can transfer itself from one computer to another. Computer viruses are dangerous to any organization and can make a company cone’s normal operations to a stand-still. When a computer virus finds its way into a company’s network, it might lead to a series of problems. A computer virus can erase important data from the company’s website, and it can also steal and manipulate secure information from the organization’s network(Misra et al., 2014). A virus can freeze the normal functions of a computer, which will alter the effectiveness of the device in the company. Therefore, to prevent a network from being infected by a computer virus, most companies have opted to use anti-virus programs and set up strong firewall systems to prevent the virus from affecting the computer network.
A trojan horse malware is a computer malware that allows hackers to access a computer using a back door like the historical trojan horse in the Greek stories that was used deceptively to lead to Troy’s fall. A trojan horse malware comes in the form of a computer application or program that the user downloads or installs in their device, unknowing its hidden intention (Nari & Ghorbani, 2013). The malware may pop-up as ads or emails that were not expected and once, they have been opened or installed in the device, they can be used by cyber thieves or hackers to breach the system or computer network. Therefore, employees who handle computer devices in an organization should be advised not to open any unnecessary online files or applications using its devices.
A worm is a computer is malware that replicates itself to other computers in the same system. A worm is one of the most common malwares in computer network security. Unlike a virus, a worm can make copies of itself to other computers in the network, but a computer virus requires a host to move from one computer to another. A worm focuses on exhausting a shared network’s bandwidth and hard drive (Bazrafshan et al., 2013). Therefore, making copies of itself can fill up the hard drive with unnecessary files that will cause the network to overload and eventually collapse if unattended.
Additionally, a computer worm can steal and manipulate data in a system. Usually, a worm finds its way into a system through spam files and emails that were not expected. Therefore, IT experts advise staff to avoid using and opening up unexpected files using the company’s computers.
Spyware is another type of malware used to spy on the user without the user’s knowledge. Cyber thieves can use spyware malware to steal information from a device and corrupt data from a shared network while using the user’s data. Spyware malware is so malicious that hackers can use it to incriminate someone using their personal information(Misra et al., 2014). Spyware can track down someone’s personal information, including social media content, credit card statements, and identity. Therefore, when one realizes that spyware malware has infected their device, they should use anti-spyware removal software to ensure that their devices are free from foreign eyes.
Working Definitions
In conclusion, malware is one of the commonly used terms in computing today to address the aspect of computer network security. Therefore, since cybersecurity has become one of the main concerns in most organizations, it is necessary to address these malware issues and develop solutions to prevent such infections in organizations’ computer networks.
Reference
Bazrafshan, Z., Hashemi, H., Fard, S. M. H., & Hamzeh, A. (2013). A survey on heuristic malware detection techniques. IKT 2013 – 2013 5th Conference on Information and Knowledge Technology, 113–120. https://doi.org/10.1109/IKT.2013.6620049
Misra, A. K., Verma, M., & Sharma, A. (2014). Capturing the interplay between malware and anti-malware in a computer network. Applied Mathematics and Computation, 229, 340–349. https://doi.org/10.1016/j.amc.2013.12.059
Nari, S., & Ghorbani, A. A. (2013). Automated malware classification based on network behavior. 2013 International Conference on Computing, Networking and Communications, ICNC 2013, 642–647. https://doi.org/10.1109/ICCNC.2013.6504162
Summary of Shin et al.’s “A First Step Toward Network Security Virtualization: From Concept to Prototype”
TO: Prof. Ellis
FROM: Tarin Sultana
DATE: 03/03/2021
SUBJECT: 500-Word Summary of Article About Network Security
The following is a 500-word summary of a peer-reviewed article about how to secure virtualized network using Network Security Virtualization (NSV). The authors introduce a new method of network security virtualization using NETSECVISOR with the least management cost. According to the authors, “The main goal of this work is to propose a new idea, network security virtualization (NSV), and design a prototype system (with the name of NETSECVISOR) that can enable NSV in cloud-like networks to help all tenants easily use security services.” (Shin et al., 2015). To demonstrate the usefulness of Network Security Virtualization (NSV), network security follows two strategies: (i) transparently monitoring flows to preferred network security providers and (ii) allowing network security response functions on a network computer. As an example of NSV setup, some essential elements are necessary, such as six routers (R1 – R6), three hosts (H1 – H3), 2 VMs (VM1 and VM2), and a Network Intrusion Detection System. By blocking network packets from each infected host, NETSECVISOR protects corrupted VMs from a network. Network security virtualization has two main functions: (i) transparently transmit network flows to desired security devices, and (ii) allow security formulas in network devices when required. Software-Defined Networking (SDN) is an evolving network technique that allows management network flows and tracks for overall network status efficiently. Five main functions of NETSECVISOR. (i) System and policy manager, (ii) Routing rule generator, (iii) Flow rule enforcer, (iv) Response manager, and (v) Data manager. A cloud administrator must use a simple script language that requires (i) system ID, (ii) device form, (iii) device position, (iv) device mode, and (v) supported functions to register existing security devices with NETSECVISOR to use them. After registering security devices for a cloud network with NETSECVISOR, it will show the security devices’ details to users using the cloud network. For security requirements, NETSECVISOR should consider the following two factors: (i) network packets should pass through specific security devices, and (ii) The network packet routing paths have to be developed and optimized. NETSECVISOR allows for introducing five security response techniques that do not necessitate installing physical security equipment or improvements to network configurations for packet handling. There are two modes of operation for these methods: passive mode and in-line mode. To check the adequacy and effectiveness of NETSECVISOR, there are three different network topologies, but two are for a virtual network environment, and another is a commercial switch environment. NETSECVISOR can construct a routing path in 1 millisecond, which translates to 1,000 network flows per second. Each topology’s CPU and memory consumption overhead are also assessing. When NETSECVISOR creates routing routes, it adds overhead. A comprehensive cloud network has millions of clients and virtual machines, and each routing path can be generated independently and asynchronously. NETSECVISOR prototype is easy to use, and clients can quickly build their own security rules; users have more choices for system types, traffic types, and response activities. Also, NVS can virtualize security resources and functions and provide security response functions from network devices as needed.
Reference
Shin, S., Wang, H., and Gu, G. (2015). A first step toward network security virtualization: From concept to prototype. IEEE Transactions on Information Forensics and Security, 10(10), 2236-2249. https://doi.org/10.1109/TIFS.2015.2453936



