00:00 City Tech Writer Opportunity (Deadline extension to Nov. 30)
07:28 Using Doodle to Coordinate Team Meeting Times
23:35 Research Report
01:10:00 Weekly Writing Assignment
Week 12, Weekly Writing Assignment
For this week’s weekly writing assignment, your team should have emailed your topic to Professor Ellis beforehand.
Please watch this week’s lecture before proceeding.
Then, one team member should create a Google Doc and share it with all team members. See this week’s lecture for instructions on doing that. Team members will need to tell whoever takes point on this their Gmail/Google Drive email addresses.
Next, copy-and-paste the outline for your analytical research report that I provided below in the “Week 12, Project, Focusing on the Analytical Research Report” post below. This document is now where your team will write together–share research, write the report, format it, etc. You can write all at the same time or you can write at different times. Do not be afraid to edit and add to this document.
Finally, one team member should create a sharable link for viewing, again, refer to this week’s lecture for instructions on how to do this, and email that link to Prof. Ellis (jellis at citytech.cuny.edu). Be sure to cc your other team members on that email so that they know it has been sent.
Week 12, Project, Focusing on the Analytical Research Report
As discussed in the Week 12 lecture, your team needs to quickly choose a topic and begin working together to do the research and writing of your analytical research report. As I discuss in the lecture, this is a secondary research report, meaning it is based on research that you find done by others. You are not required to perform primary research or building/testing your topic on your own. This is the foundation for the rest of your collaborative project, which also includes a presentation, a website, and report on collaboration. I will discuss these latter parts next week.
With your analytical research report problem/topic identified, you can begin researching it with the library’s databases and books, periodicals like the New York Times, and the World Wide Web.
Evaluate and vet your sources so that you can account for their veracity, accuracy, credibility, etc.
To get started with writing your report together, check out this week’s Weekly Writing Assignment and the lecture. You will need the following outline:
Introduction (topic and why your report is important) Objectives of the research (what were you attempting to do?) Method (methodology–what kinds of research did you do, how did you do it, and why is the research sound?) Results (what did you find in your research? facts, quotes, figures, interviews, surveys, etc.) Discussion (how do you interpret your results? what story does your data tell us? results and discussion can be combined, but title this section appropriately if you do so) Conclusions (what conclusions do you draw from your results and discussion? what is the significance of what you discovered?) Recommendations (what do you think should be done to solve the research problem based on your research? this section is what all of your work is leading up to.)
Also, here are some resources and examples that I discussed in this week’s lecture to help you with writing and designing your analytical research report.
- Doodle (for finding meeting times for your team)
- Explanations of report parts (look under Primary Research Report, but remember you are writing a secondary research report)
- Example Student Research Report on Solar Panel Manufacturing and Waste
- Example Student Research Report on 5G
- Sample Research Report (note the layout and design)
Albert Chan’s Expanded Definition of Machine Learning
Introduction
The purpose of this 750-1000-Word Expanded Definition is to explore the definition of the term “machine learning” with regards to the scientific community and society. I will be analyzing the term in a study on fairness, education, and machine translation. My working definition will be provided afterwards.
Definitions
In the article “A Snapshot of the Frontiers of Fairness in Machine Learning” by Alexandra Chouldechova and Aaron Roth, the definition of machine learning is straightforward. “Machine learning is no longer just the engine behind ad placements and spam filters; it is now used to filter loan applicants, deploy police officers, and inform bail and parole decisions, among other things.” (Chouldechova, Roth, 2020, p.82). To Chouldechova and Roth, machine learning is a process that has evolved to automate more complex data.
On the other hand, the New York Times article “The Machines Are Learning, and So Are the Students” by Craig S. Smith defines the term differently. “Machine-learning-powered systems not only track students’ progress, spot weaknesses and deliver content according to their needs, but will soon incorporate humanlike interfaces that students will be able to converse with as they would a teacher.”(Smith, 2019). According to this, it can be seen that Smith defines machine learning as a means to an end, and this end being helping students learn better.
As for the article “On the features of translationese” by Vered Volansky, Noam Ordan, and Shuly Wintner, machine learning is a simple one. “In supervised machine-learning, a classifier is trained on labeled examples the classification of which is known a priori. The current task is a binary one, namely there are only two classes: O and T.”(Volansky, Ordan, Wintner, 2015, p. 103). To Volansky et al., machine learning is an assisting tool to help create more humanlike translation and must be supervised in order to function correctly.
Context
The context of all three articles is quite simple. The quotes I have used above are the most relevant to the topic of choice, as well as definition since machine learning wasn’t clearly defined in each article. So I will bounce off of that.
In the first article, the context used is a scholarly article searching into how machine learning can be made “fair”, or better put, “objective”. “With a few exceptions, the vast majority of work to date on fairness in machine learning has focused on the task of batch classification.”(Chouldechova, Roth, 2020, p.84). For better or for worse, the quote tells us that fairness has typically through batch classification. Batch classification, in this context, is sorting data by inputting user-defined characteristics and then judged through user-defined fairness. Machine learning is just the process of automating this process and even “learning” how to do it with other types of data. But the fallacy of fairness with such a method is laughable since humans are the ones defining fairness. Since humans have inherent bias, fairness is difficult to judge.
In the second article, it is a news article speaking about technology in education, specifically, machine learning and how beneficial it is for teachers. “The system also gathers data over time that allows teachers to see where a class is having trouble or compare one class’s performance with another.”(Smith, 2019). For teachers, this system is a way to track a student’s progress or performance without having to personally analyze the sheet data.
For the last article, the context is the machine translation. What should come to mind when hearing the term machine translation should be famous web browser-based translation services such as Google Translate, Niutrans, Sougou, and DeepL. That’s about it.
Working Definition
Personally, I am majoring in Computer Systems: IT Operations track. However, I have a hobby in translation with the assistance of machine translation. So, my working definition for machine learning is “the application of gathering vast amounts of data, categorizing the data, sorting them out, and analyzing data to find out the psyche of people.” For example, if given a group of 100, the data collected must be categorized by their gender or whatever category is set. Then, the answers gathered will be sorted by correct/incorrect based on the generally accepted answer. Finally, the data is analyzed so that there are percentages of what questions were answered correctly most of the time based on the sorted category. With that, the machine has a sample of what to expect if someone of x category answers the same data collection set. Done on a macro-scale, the machine will be able to predict what a population’s answer could be.
References
Smith, C. S. (2019, Dec. 18). The Machines Are Learning, and So Are the Students. New York Times. https://www.nytimes.com/2019/12/18/education/artificial-intelligence-tutors-teachers.html
Volansky V., Ordan N., Wintner S. (2015). On the features of translationese. Digital Scholarship in the Humanities, 30(1), 98–118. https://doi.org/10.1093/llc/fqt031
Chouldechova, A., Roth, A. (2020). A Snapshot of the Frontiers of Fairness in Machine Learning: A group of industry, academic, and government experts convene in Philadelphia to explore the roots of algorithmic bias. Communications of the ACM, 63(5), 82–89. https://doi.org/10.1145/3376898
Week 11, Office Hours, Cancelled
Dear all,
I’m afraid that I’m too ill to hold office hours today. Please email me with your questions and I’ll get back to you in the next couple of days. My email address is jellis at citytech.cuny.edu.
Best, Professor Ellis
Week 11, Lecture
Greetings, all!
Make sure you watch and take notes on this week’s lecture. It covers submitting your Instruction Manual Project and beginning the Collaborative Project. Scroll down our OpenLab Course Site for detailed instructions and screenshots to help you with those things, too. And, watch for my emails that will announce your new teams for the Collaborative Project.
Office hours will be Nov. 4 from 3:00-5:00pm. I’ll post a link above beforehand.
Week 11, Weekly Writing Assignment
To begin your team’s collaborative project, the first things that you will need to do are: 1) introduce yourselves, 2) provide other contact info, and 3) choose a topic for your research report.
To accomplish these things, I will start a new email thread for each collaborative project team (remember that these teams are different than your peer-review teams).
During this week, each team member should “Reply All” to my email to introduce yourself (including your major, hobbies, and interests, and make a note if you already know someone in your team–perhaps from the peer-review teams or another class), provide a phone number or suggest another way for your teammates to communicate besides email (Facebook, Whatsapp, etc.), and list three possible scientific or technical problems that you can potentially research for your team’s research report (for example, Moore’s Law, specific computer exploits like rowhammer or types of exploits like privilege escalation, etc.).
The purpose of your report is to present what you can learn about the problem and provide some solutions also based on your research, so think about these possible problems based on your studies and interests. Since you are all studying computers and/or electrical systems, I would recommend that you focus on problems related to that instead of problems not directly related, such as global warming. Coming up with three possible problems might require a little bit of library research, so don’t be afraid to check out the databases!
Now, after you and your teammates begin exchanging these emails, look at the possible problems for similarities or connections. Everyone should reply all to comment on the problems, generating ideas, and arguing for or against some of the options. After this discussion, a clear winner might emerge, or one team member can devise a vote of the top two or three candidates.
At this point or even before after you’ve made your first introductions via email, your team can decide if they would like to hold the rest of the conversation over email or another communication medium of your choice. For the weekly writing assignment, I will be looking for your first email with your three possible problem topics. The rest of the conversation is for your benefit to choose a topic for your project by Wednesday, 11/11.
After you’ve selected a problem for your research report, I would like one member of your team to send me an email and cc (carbon copy) all the other team members on that email. In the email, let me know what scientific or technical problem your team has selected. Email me your team’s topic by Wednesday, 11/11.
Watch this week’s lecture for more details and explanation. I will post it on Wednesday following our established schedule.
Week 11, Project, Beginning the Team-Based Collaborative Project
While you are finishing up your last individual project in the class, we are moving ahead to begin the team-based collaborative projects in the class.
Think of each of the following projects as part of an interconnected larger project. Each team member should contribute to each part, but individual team members may take the lead on one part versus the others depending on their skill set and interests. For example, one team member may take the lead on the research report and collect contributions from the other team members for the first draft, and another team member may take the lead on the presentation or the website.
These are the parts of the collaborative project from the syllabus:
- Collaborative: 4000-6000-Word Analytical Research Report, 20%
- Each team member contributes 1000-1500-word contribution to a 4000-6000-word analytical research report on a scientific or technological problem that demonstrates: 1) knowledge of the history and context of the problem, 2) knowledge of the causes and nature of the problem, 3) ideas for solving the problem, 4) the ability to explain the problem and offer possible solutions to a general audience, 5) the ability to integrate written work with the written work of a partner or partners in a coherent report, and 6) knowledge of proper research report format. At least six library-sourced citations must be included (non-library-sourced citations are encouraged, but they do not count toward the six library-sourced sources). Any outside sources cited should be documented according to APA format.
- Collaborative: Seven-to-Ten-Minute Oral Analytical Research Report on a Scientific or Technological Problem, 10%
- The goal of this part of the project is to transform your written report into an spoken presentation anchored by a PowerPoint or other visual presentation supplement. As a team, adapt and present your analytical research report as an oral presentation that demonstrates: 1) knowledge of oral presentation techniques and conventions, 2) the ability to organize a presentation effectively, 3) the ability to incorporate various media into the presentation, including appropriate computer software, 4) awareness of audience, 5) the ability to communicate the value of the product or service in clear spoken English, 6) the ability to answer audience questions, 7) the ability to collaborate productively with a partner or partners, and 8) the ability to explain the problem and offer possible solutions to a general audience.
- Collaborative: Website Advertising a Product or Service Responding to the Analytical Research Report and Oral Presentation, 10%
- The goal of this part of the collaborative project is to imagine a service or product that your team can offer that is related to your research report and oral presentation, both of which will be featured on the website in some way. The website should demonstrate: 1) knowledge of the product or service offered, of pertinent market forces, and of the potential customer base, 2) basic knowledge of web page design and composition, including appropriate software. The website will be based on your presentation and it is encouraged to be integrated into your presentation (perhaps to demonstrate how your team is promoting your product or service). All graphics, logos, design, and text must be created by your team.
- Collaborative: 500-Word Report on Collaboration, 10%
- During the collaborative project, the team as a whole needs to track and document their progress, challenges, and successes, and each individual delegated responsibilities needs to keep track of what they contribute to the project. As the last component of the collaborative project, write a brief report of 500-750 words reflecting on how the team worked together and what each individual team member contributed to the overall effort. Each team should submit only one report.
Another way to consider these interconnected projects is through the following illustration:
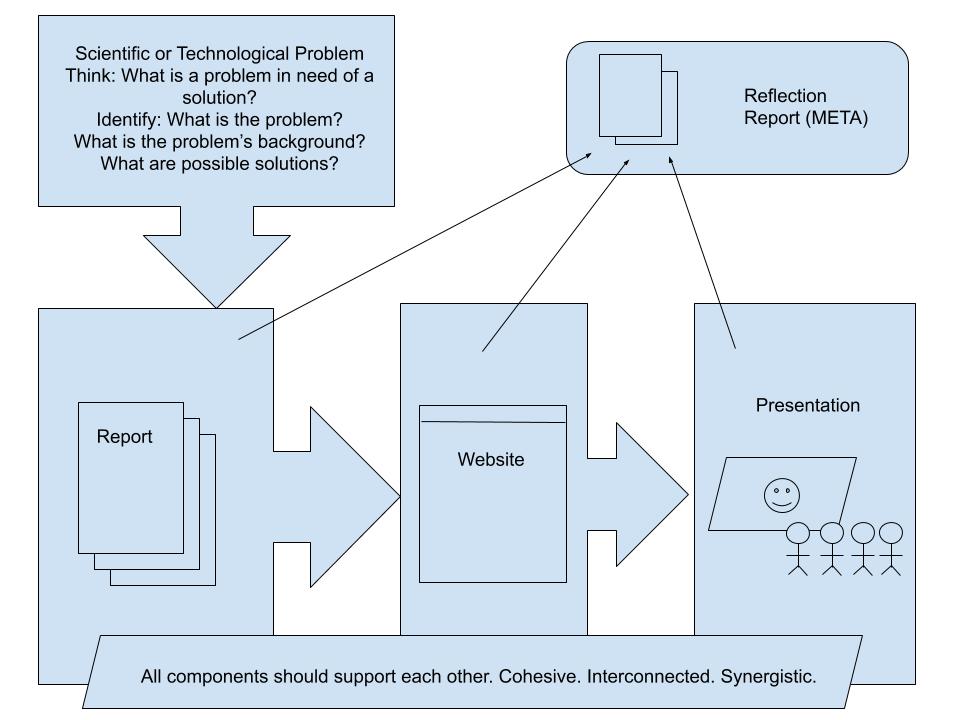
The main part of the collaborative project is the research report. It anchors everything else. It should be completed first and adapted or transformed for use in the other deliverables: the website and the presentation. The report, website, and presentation will be submitted on our OpenLab Course Site. Also, throughout the project, the team should keep track of the work that each person does and compile that into a reflection report that will be submitted via email to me after your collaborative project is completed.
To distribute the workload better, you will work in a new team of five or six persons. These teams are randomly assigned using a number list that I generated on random.org.
For your reference, I am including the teams below. I will get in touch with each team via email for this week’s weekly writing assignment.
Remember, don’t confuse these teams with your peer review teams on the first three projects in the course. If you are still working on individual projects and need peer review feedback, you should give and receive it with your peer review teams that you’ve already been working with.
Separately, you will begin working with this new team on the collaborative projects. There may be some overlap between your peer review team and the new collaborative teams–this was just by chance and not by design. In addition to reaching out to you by email, I will detail how I would like you to begin the project together in this week’s Weekly Writing Assignment, which I will post soon.
And, make sure that you all watch this week’s lecture and listen carefully to the details that I provide about the collaborative project.
Team 1 Barbu L. Tan Arias Romanowski Clarke Beauge Team 2 Requena Dominique Barbu T. Anny Anika Team 3 Abdulla Persaud Ferreira Patterson Htut Team 4 Andiappen Cifuentes Chan Pritom BK Team 5 Adeyemi Campbell Su Lin Bah
Week 11, Project, Submitting Your 1500-2000-Word Instructional Manual Project
While we will be moving ahead to the final, collaborative projects in the class this week, I wanted to go ahead and provide you with instructions for submitting your 1500-2000-Word Instructional Manual.
Since we are running a week behind on the syllabus, your instructional manual is now due by Nov. 11. If anyone needs additional time, reach out to me at jellis at citytech.cuny.edu and let me know how much more time you need to complete the project.
To submit your Instructional Manual, please do the following (which I will also discuss in this week’s lecture).
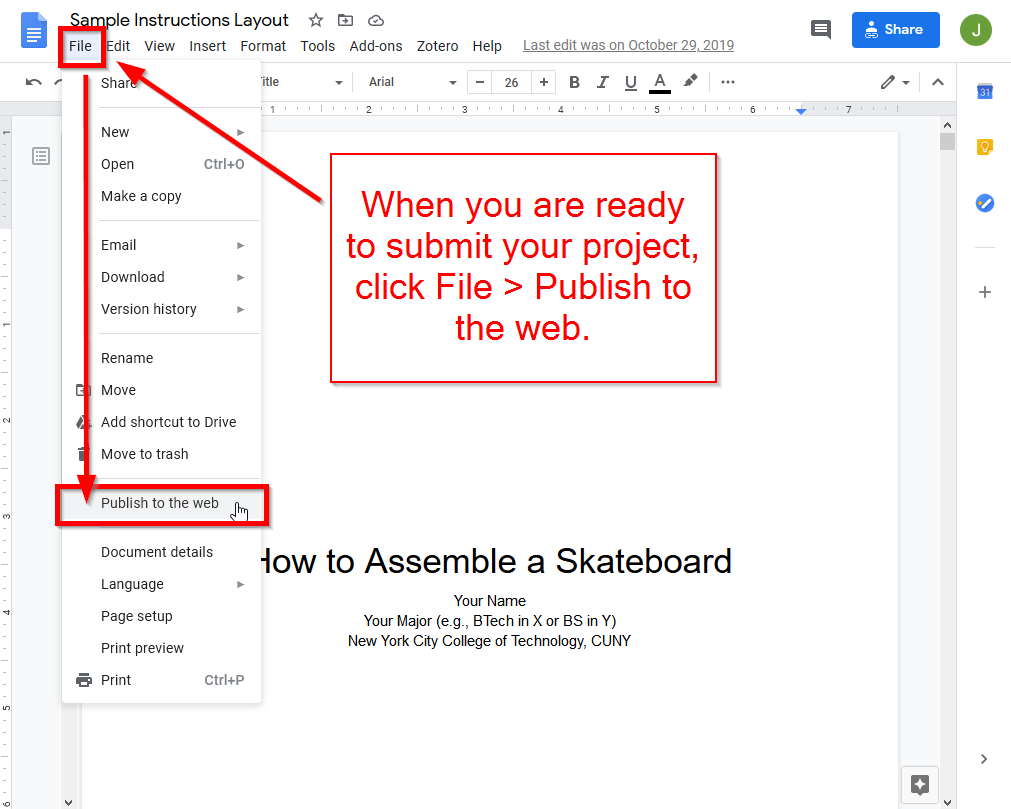
First, you need to publish your Instructional Manual to the Web from inside Google Docs. This is a great feature of Google Docs that I wanted to make you all familiar with. Essentially, it allows you to quickly publish content on the World Wide Web from Google Drive (Docs, Sheets, and Present). To do this, follow these steps:
After opening your instructional manual in Google Docs, click on File > Publish to the web as shown below.
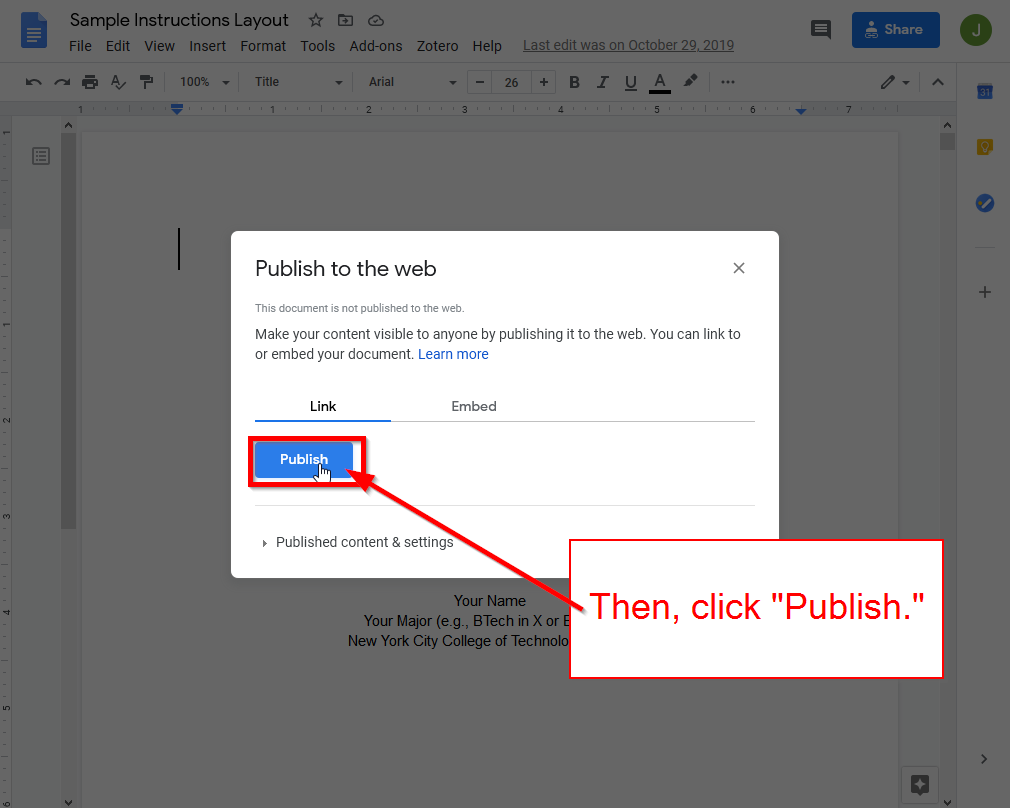
Then, click “Publish.”
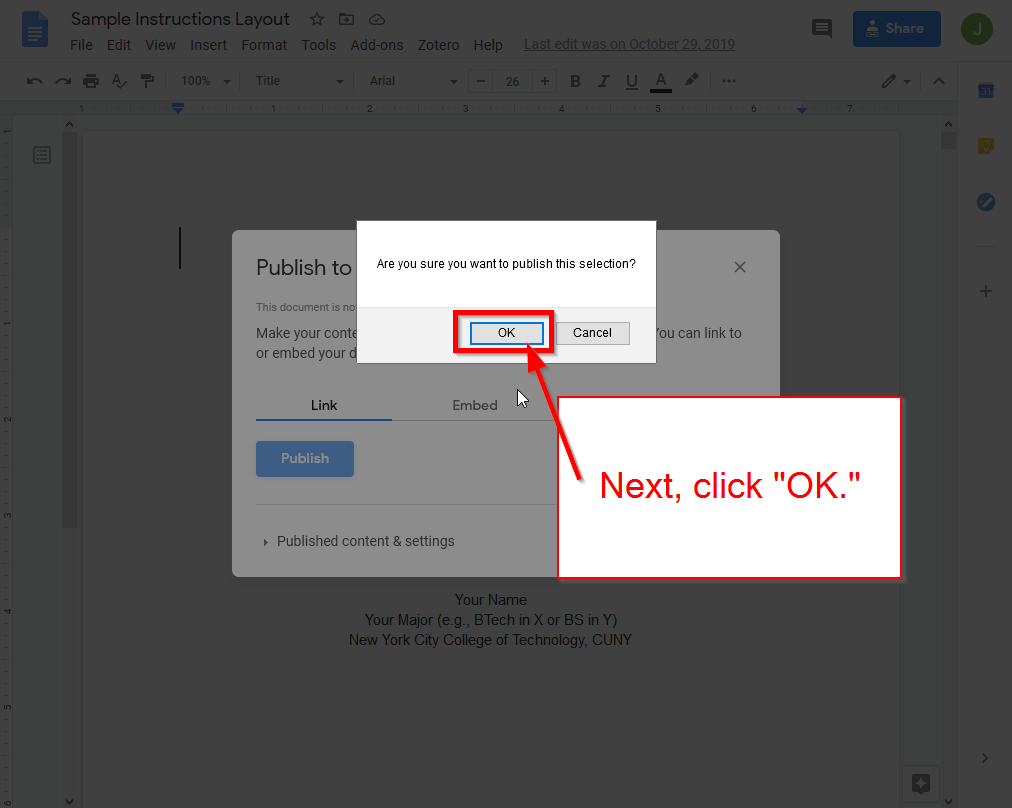
Next, click “Ok.”
Finally, copy the link to your now published instructional manual and click the “x” in the upper right corner to return to Google Docs.
That completes the first half of this process.
The next phase is creating a post on our OpenLab Course Site that includes the link that you just copied. To do this, open another tab in your web browser and go to our OpenLab Course Site. Then, click the “+” icon to create a new post as shown below.
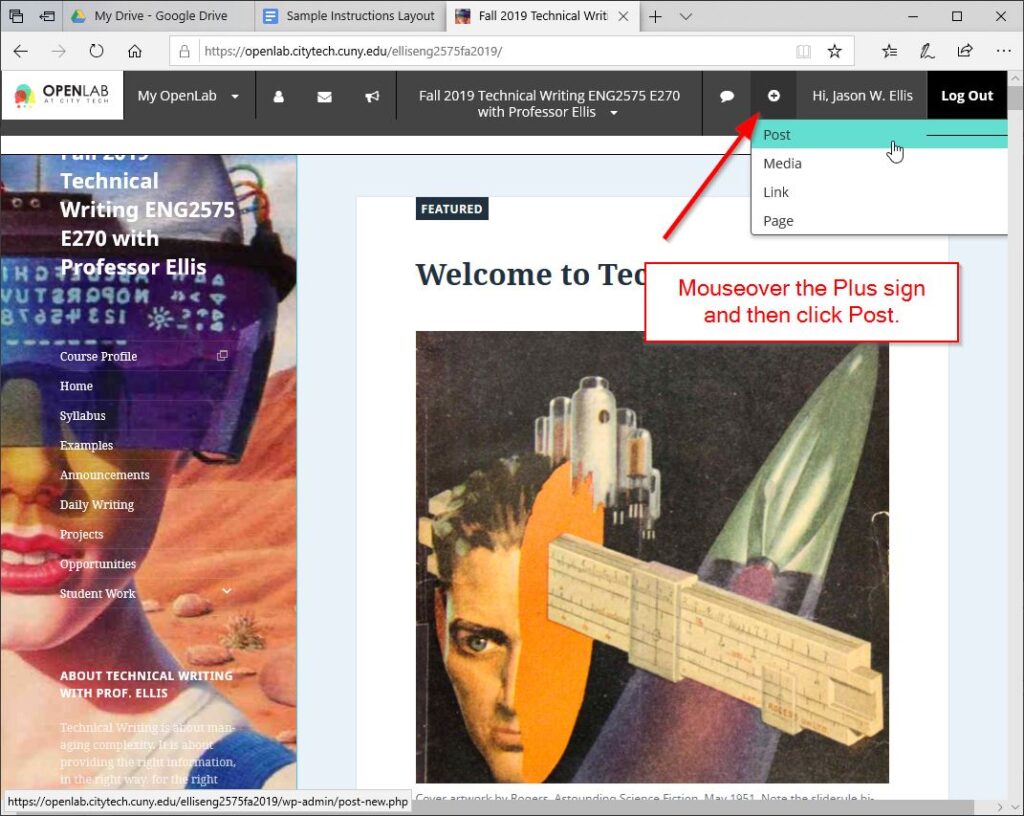
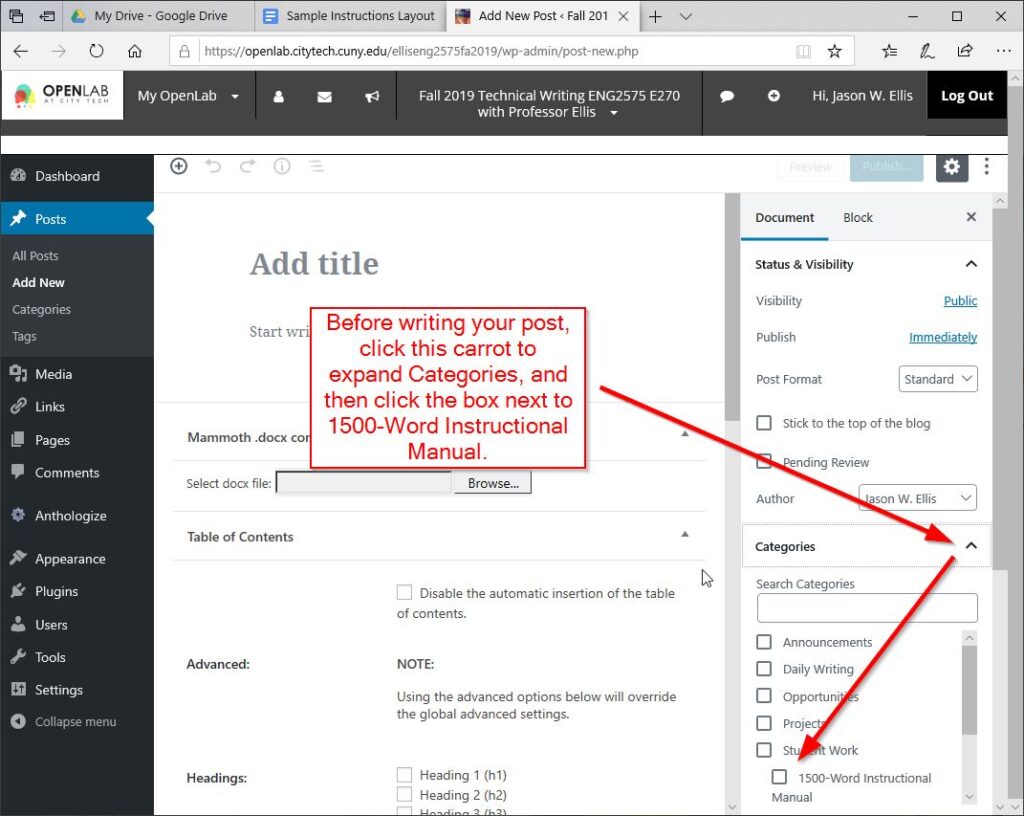
Then, add a check next to “1500-Word Instructional Manual.”
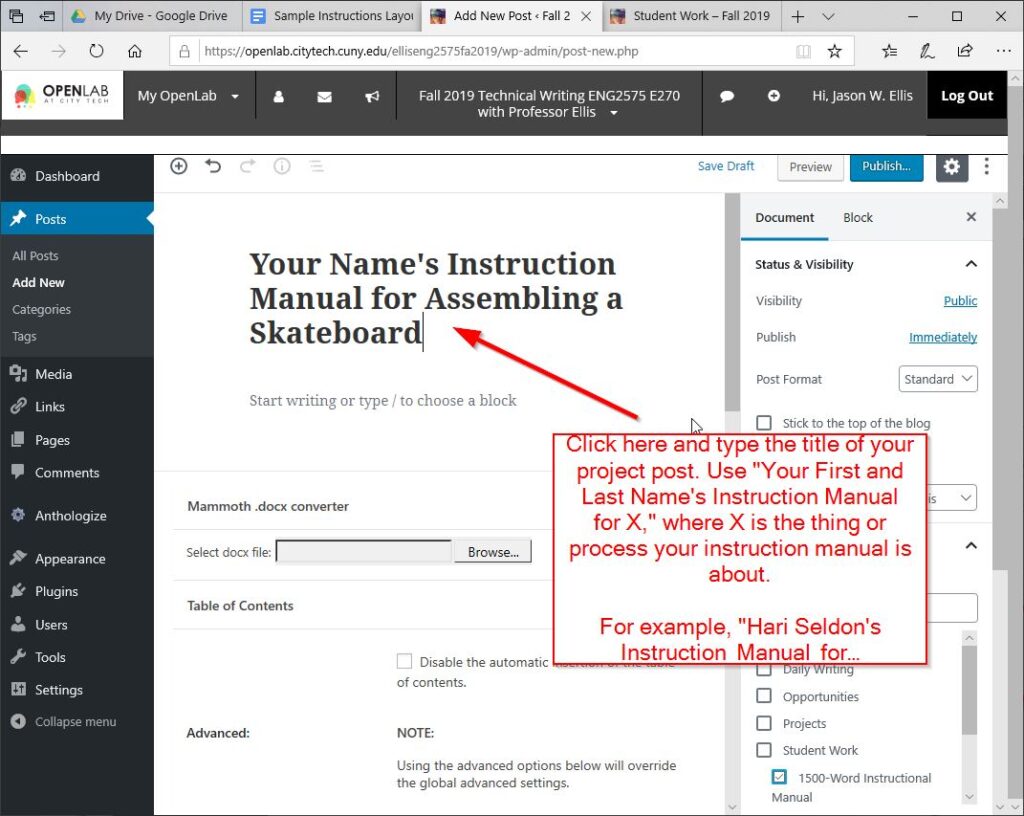
Then, type in a title for your post that includes your name and a descriptive title, such as “Jason Ellis’s Instruction Manual for Assembling a Skateboard.”
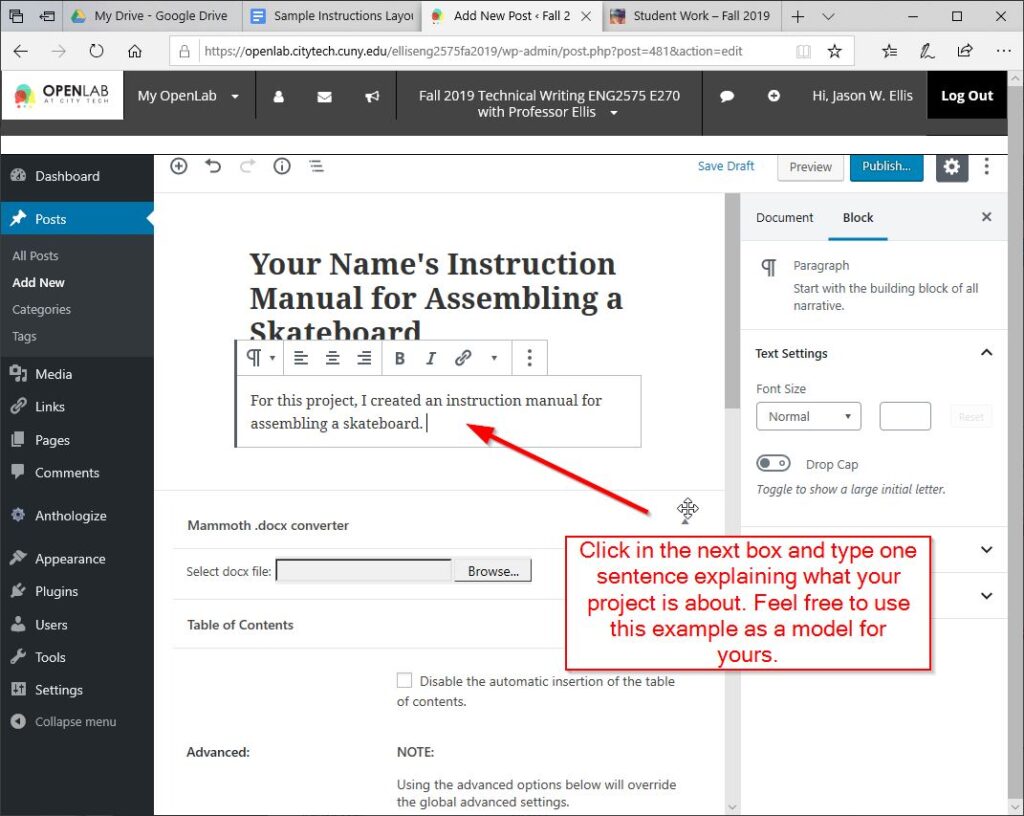
Next, add a sentence into the body of your post describing your project, such as “For this project, I created an instruction manual for assembling a skateboard.”
Then, highlight the part of your sentence that corresponds with “an instructional manual for [your topic].”
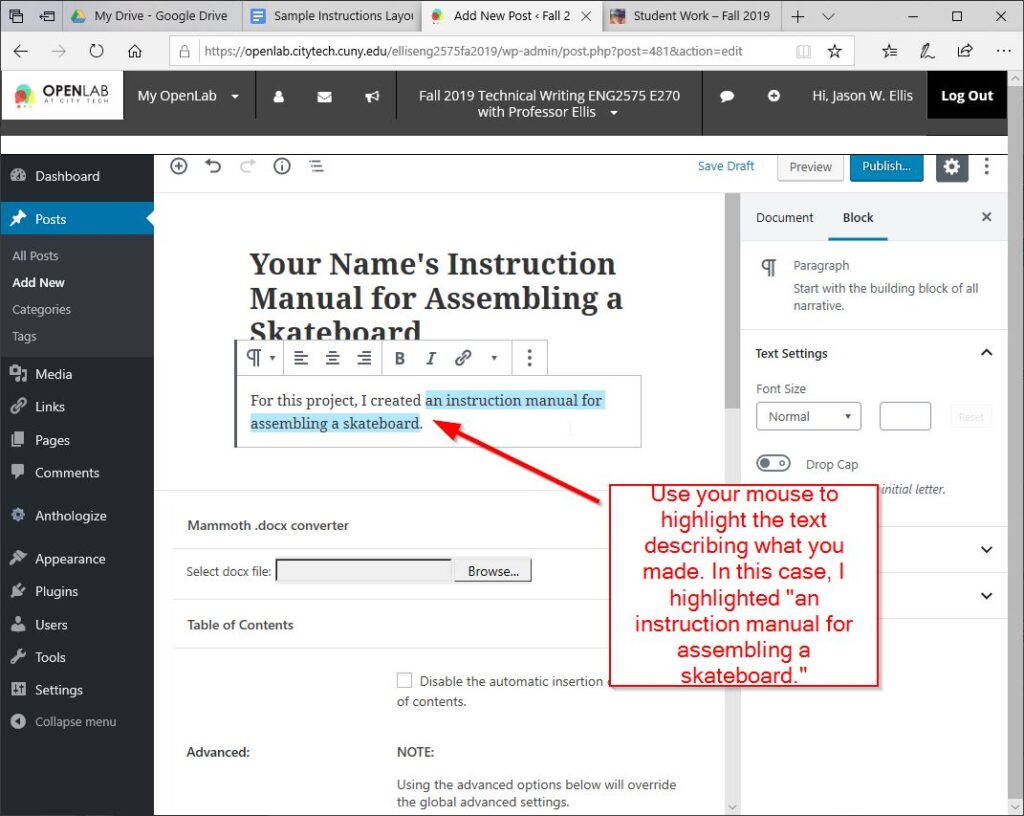
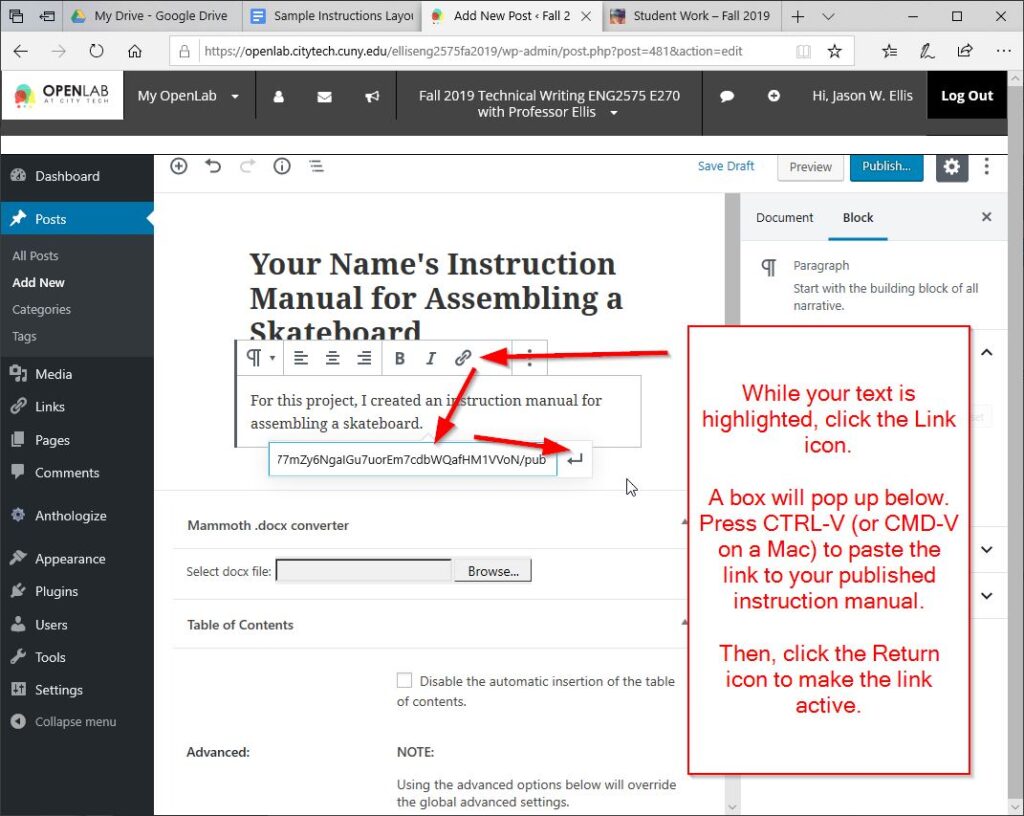
Next, click the icon above the text that looks like three chain links, paste your link into the box that appears, and click the “Enter” or “Return” line-and-arrow icon to the right of the link as shown below.
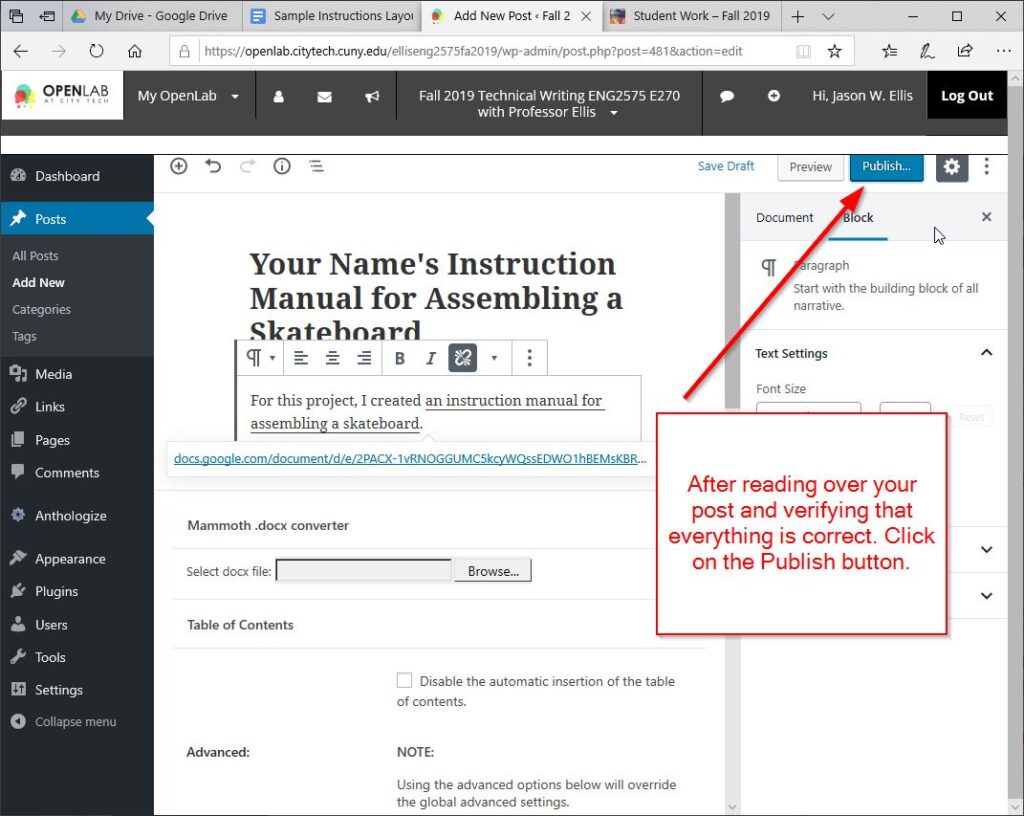
After reading over everything and correcting as needed, click the “Publish” button in the upper right corner of the page.
And, click “Publish” again to confirm.
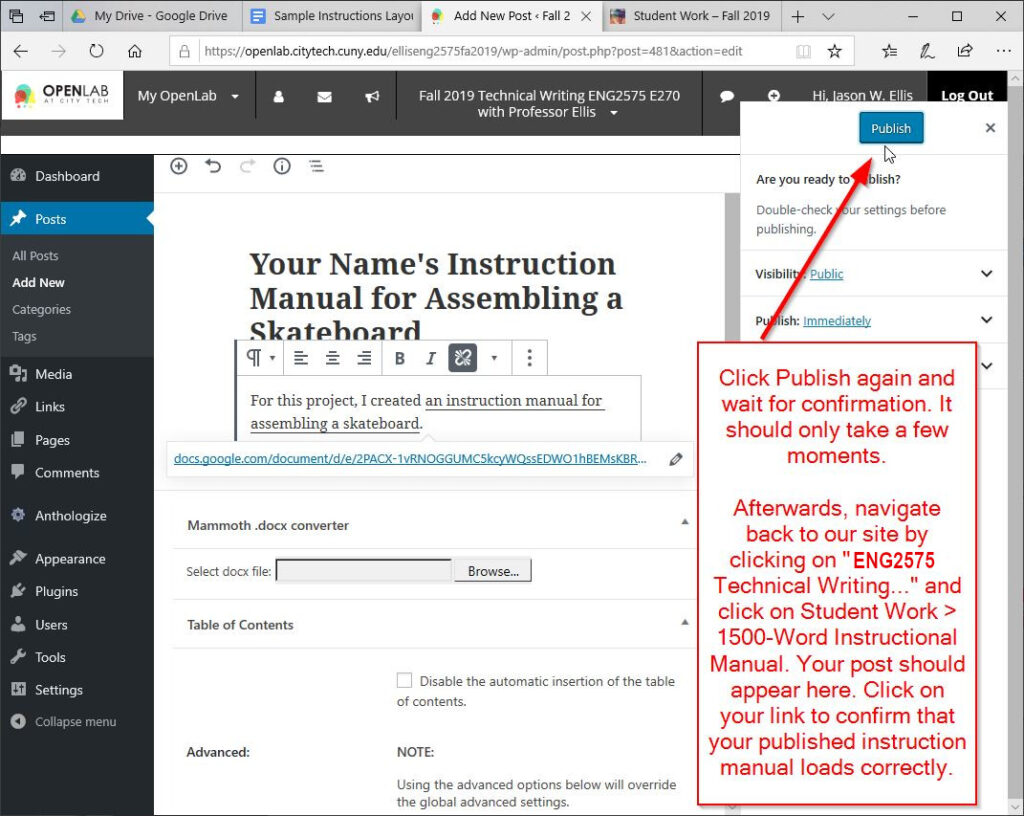
To see if your post is live, click on the title of our OpenLab Course Site in the center of the page, click on down carrot next to Student Work in the left menu, and then click on “1500-Word Instruction Manual.” Yours should be at the top of the posts that appears.
Nargis Anny- Professor Jason Ellis- New York City College of Technology – ENG2575 OL70-10/13/2020 …Cyber Security Cyber Security is the process of protecting various technological programs, systems and networks from viruses and other digital issues. The viruses are often set up by anonymous people who are looking to gain user information, disrupt the hardware setup as well as delete data. Now as technology develops in today’s age, so do the viruses and the requests for safer online security. Cyber security started out in the 1970’s. Bob Thomas, a computer researcher associated with ARPANET (Advanced Research Project Agency Network), invented a program called “CREEPER”. The “CREEPER” program would start on a network and crossover from system to system. And it would leave a trace behind in the form of a message, “I’M THE CREEPER: CATCH ME IF YOU CAN”. The “CREEPER “eventually came to an end thanks to Ray Tomlinson. Tomlinson, who invented the email decided to evolve the CREEPER and create an equivalent program called the “REAPER”. This program managed to follow the CREEPER’s trail and delete it permanently, making the “REAPER” the first antivirus program to be created. Eventually, Thompson and Tomlinson’s creations led to various software and network companies to realize that there were numerous bugs in their systems that could be tampered with. This became more serious when organizations had computers and phone lines operating together to create networks of their own. And thus, anonymous people could gain access to their information. Spanning across from the 1980s to the 00’s, the internet began to experience more popularity around the world as technology began improving rapidly. Cyber hackers became more prevalent as computer viruses improved and couldn’t be monitored. Inventor Robert Morris created the “Morris Worm” in 1988, a program that multiplied beyond networks, foisted computer bugs and replicated it to indentify the spots in the system. However, while this worked it caused internet service to slow down and damage networks heavily. In the 1990’s, firewalls and anti-virus programs were used to help protect public user information. As we reached the 2000’s, we see more criminal hackers being taken down with longer jail time and heavier fines for their actions. However, now hackers were able to create virus programs that not only could hit users in cities, but people across various parts of the world.However, while Cybersecurtiy does help, there are some setbacks. Security software often slows down computers and their network. A lot of people who use it are bound to have their personal data exposed to tons of people, who can use it for any reason. Technology users have been introduced to numerous cyber security threats such as Malware, Ransomware, Phishing and Social Engineering. With Malware, this software can tamper with user files through various codes and damage to data and network systems. Ransomware also tampers with user files, but requests a payment to gain to get back those files. Phishing is known for having various scam emails be sent to users under the guise of a legitimate source and steal information (address, card information, phone number, login information) once someone opens it. Social engineering is when someone manages to gain user information in person and use it for their own purposes. An example of this can be shown with credit card scammers. These people are known to ask associated for their card information to buy various goods, such as clothes, jewelry, cars or even houses and instead that person’s information and money is stolen. Even with the millions of dollars that go towards new security programs, there will always be something out there that tops it. In today’s time, technology researchers are looking towards using methods that would identify online users tech patterns, and prevent the threats from getting to them in the first place. To conclude, Cyber Security is something that will progress over time, and so will the viruses that can harm it. Despite this being an unfortunate reality, the best thing to do is to always be on top of any computer virus that is created. That’s all we can do as tech users. As we see Cyber Security, increase, we can hope for a program that wipes out any virus instantly and keeps the computer functioning at 100 percent.
Sources:
I. Margaret Rouse
What Is Cybersecurity? Everything You Need To Know
https://searchsecurity.techtarget.com/definition/cybersecurity?amp=1
April 03, 2020
II. Dakota Murphey
A History of Information Security – IFSEC Global: Security and Fire News and Resources
https://www.ifsecglobal.com/cyber-security/a-history-of-information-security/
June, 27, 2019
III. defined, explained, and explored
IV. What is Cyber Security?
https://www.forcepoint.com/cyber-edu/cybersecurity



