In an autonomous car, there is a decision-making algorithm. It decided when to go, stop, merge, turn, and other physical driver decisions. This algorithm is primarily hypothetical and not theoretical. A human will think of multiple solutions and can think quickly on their feet, whereas a hypothetical algorithm will have to cycle through all the possible decisions to find just the one to deal with in real-life situations. The algorithm is also hackable and doesn’t assure vehicle safety for consumers when hacked (like stopping the vehicle in mid traffic or speed, crashing into other vehicles, hitting pedestrians and so much more)
Solution 3: Don’t Forget the Basics!
Autonomous vehicle services must make an effort to educate their customers on these vehicles and what to do in the event of emergencies (i.e., sudden failure of operation, issues with inclement weather, driving behavior compromised due to hacks, and other potential danger scenarios). Companies should create training suites online that run through all the technology that makes these vehicles operate the way they do and point out crucial devices in the vehicles and/or in the environment that can help keep both drivers and pedestrians free from potential harm.
Solution 2: Ensure Devices and Software are Cutting-Edge
All devices that assist in the provision of the autonomous driving experience, whether onboard or external (i.e., sensor nodes, traffic control devices) should be maintained wherever possible and as often as possible. Continued updates on device algorithms and authentication protocols will have a strong effect in slowing down and deterring malicious hacks, keeping software safe and securing sensitive consumer/company information.
Solution 1: Over-the-Air Updates
Self-driving car companies can use Over-the-Air updates (remote updates implemented via traffic control devices) to keep onboard device software as up-to-date as possible on a frequent basis. In doing so, gaps in the algorithms that enable the self-driving functions of these vehicles can be plugged up as quickly as possible without interrupting a client’s trip.
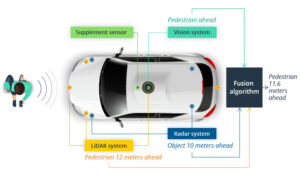
Issue 3: Sensor Data
Data is constantly being collected through self-driving sensors. These sensors are camera sensors, radar sensors, and LiDar sensors. These sensors check the surroundings of the car anything and everything it comes in contact with. That being said, this data collection is against the federal communication commission standards. Companies aren’t allowed to collect data through a wifi connection/network of any types of sensors. It’s a major security risk. Companies like google faced consequences for this violation. They put innovation before consumer’s privacy.
Issue 2 : Surveillance/Location Hacking
Self-driving cars will threaten your privacy and life. While a consumer is in the vehicle, the autonomous car immediately stores all of your information. It is holding a tremendous amount of data. You are creating an information trail of web searchers, social media posts, emails, etc. It is viewing your travel data of where you’re going at all times (what time did you leave area x, y, and z). As your location is being tracked and personal information is being stored, companies are storing your data. What will they do with this data and are they protecting it?
Issue 1 : Cloud-Computing Database
Self-driving cars are fueled by the cloud, and autonomy was made to be independent. What happens when you have connection issues? Where would all that data go to now? It has been proven many times before their clouds have been hacked. The biggest issue is not just the could database could be hacked it is the lost data that is the issue. There’s always the lack of visibility of the data and the inability to control the data.
Home
Group 1 Collaborative Project: Self-Driving Cars: Privacy and Security
This is Group 1’s collaborative project on privacy and security issues with self-driving cars. This site covers those privacy issues and potential solutions to those issues.
Project Slides: https://docs.google.com/presentation/d/1xc6slFTNh1kCsByoZTmm5nyXJtO0JXgAxei9TaE835c/edit?usp=sharing
Project Report :