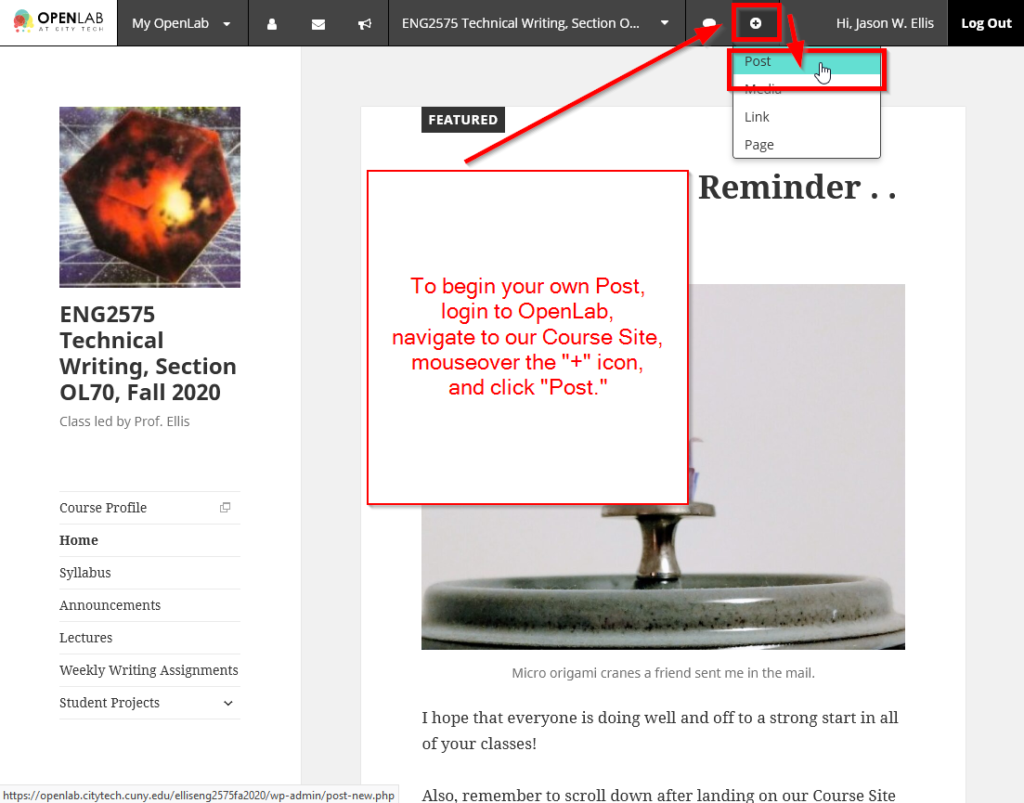
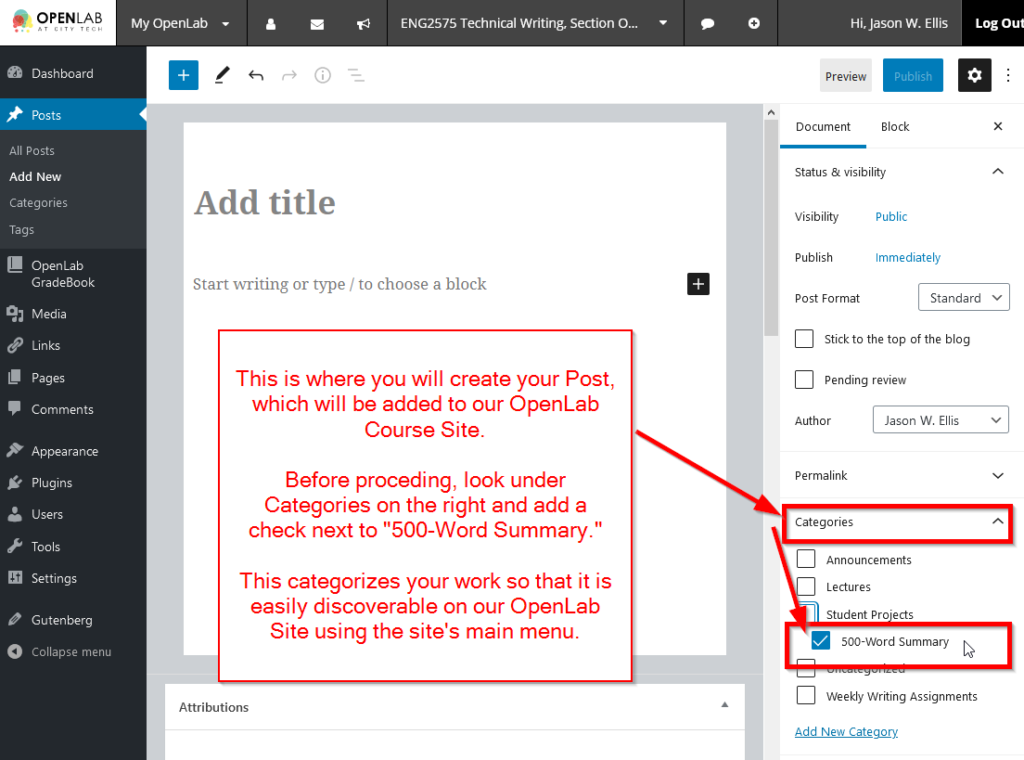
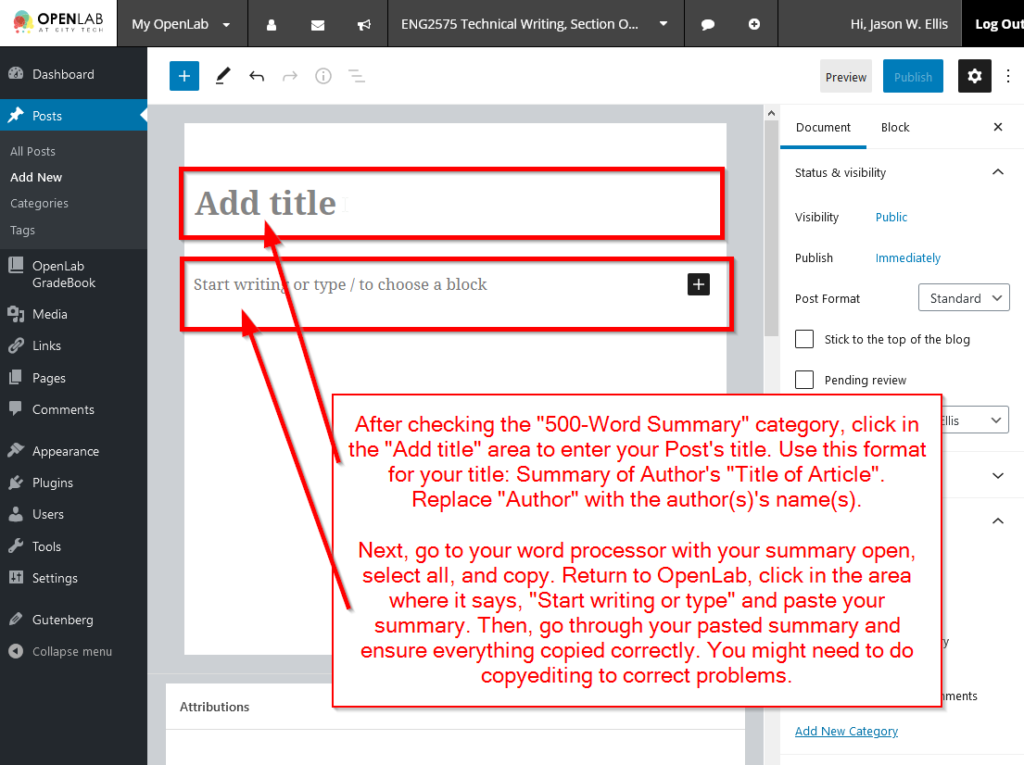
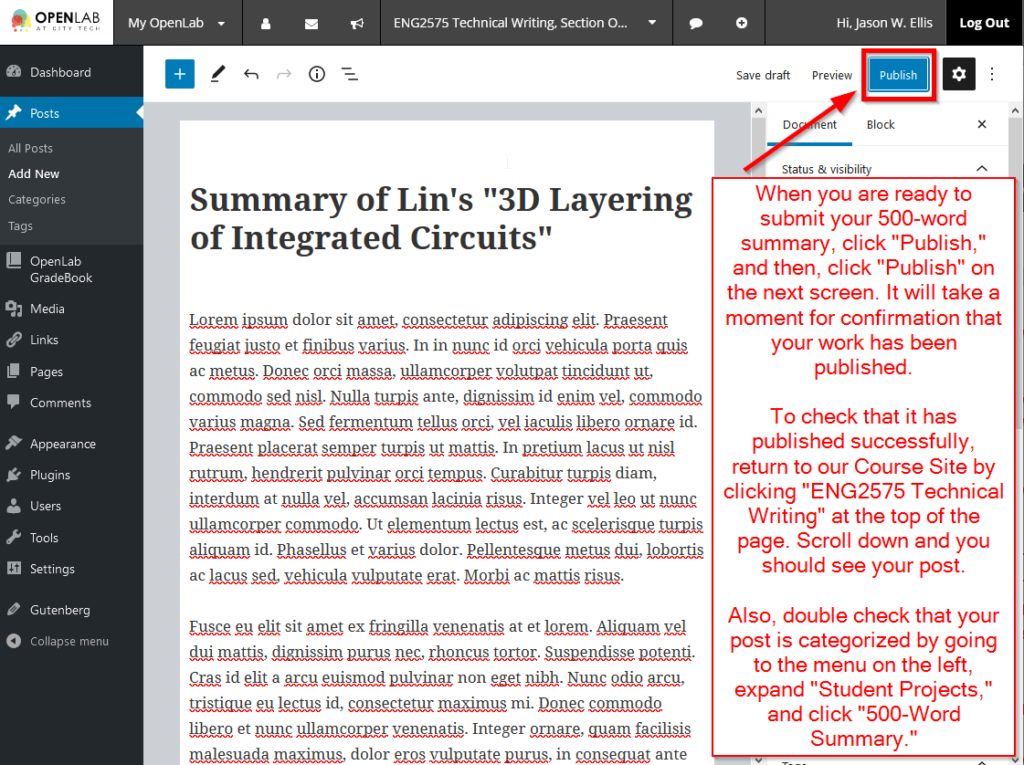
TO: Prof. Ellis
FROM: Jerry Chen
DATE: 3/3/2021
SUBJECT: 500-Word Summary of Article About Network Attacks and Preventions
The following is a 500-word summary of a peer-reviewed article about the type of attack and its prevention in nowadays’ s network. The authors discuss the types of network attacks that currently exist as most of the people or small businesses still didn’t aware of the importance of configuring their network gears, which open their doors to welcoming the attacks. According to the authors, “Any data passes over large number of workstations and routers which sometimes very weak due to organizational structures and their policies which may lead to damages and attacks” (Kandan et al., 2019, p. 2). For network security, there are two types of network securities, such as hardware security and software security. Hardware security is like the defensive system, which is often used in corporations and software security is application-based, which is only for the individual or small firm used. As mentioned by the authors, “if the system is not implemented the proper security methods and control over their network, then there is a way for attacks from internal or external using these techniques” (Kandan et al., 2019, p. 2). There are some major types of attacks that attackers used most frequently nowadays, such as browser attacks, man-in-the-middle attacks (MITM), and botnets.
Browser attack is the most frequent web browser base type of attack that the attacker uses to hack into the system by adding malware to the browser. Man in the middle attack (MITM) is another attack that the attacker uses to interrupts the confidential data during the transmission process of two victims and access to the data without the awareness of victims. The botnet is a different type of attack, which is the formation of robot and network, and it is one of the main attacks that attacker uses to gather unauthorize confidential data from the users.
The problems always come with solutions, as well as the attack techniques. According to the authors (Kandan et al., 2019, p. 4), there are some preventions which born to prevent users from getting those attacks, such as the prevention of man in the middle (MITM), HTTPS, and the prevention of botnet. To prevent getting MITM attack, the two endpoints should use the higher secure network when communicating and encrypted the transmission by using any encrypt protocol (Radhakishan et al., 2011). HTTPS is the prevention which is uses to protect users from getting browser attacks by providing a higher secure network over the browser by issuing the certificates to only the participating entities and verified at each party before the transmission. Moreover, to prevent getting botnet kind of attack, the user should make sure the intrusion system is up to date and specifically configure the ports or shut down the ports that not currently in use.
As network security constantly changing every day, attackers are always using their tech knowledge to explore new types of attacks to fulfill their purposes. People or small businesses should always configure their network gears and install security software to monitoring the attacks to decrease the chance of being attack.
Reference
Kandan, A. M., Kathrine, G. J. W., & Melvin, A. R. (2019). Network attacks and prevention techniques – A study. IEEE International Conference on Electronics, Communication and Computing Technologies (ICECCT), pp. 2,4. https://doi.org/ 10.1109/ICECCT.2019.8869077
Radhakishan, V., & Selvakumar, S. (2011). Prevention of man-in-the-middle attacks using id-based signatures. Second International Conference on Networking and Distributed Computing. https://doi.org/ 10.1109/icndc.2011.40